
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


Ascend Packet Filters
This chapter covers the following topics:
Filter overview
A filter contains rules describing packets and what to do when those packets are encountered. When a filter is applied to an interface, the MAX TNT monitors the data stream on that interface and takes a specified action when packet contents match the filter rules.
Depending on how a filter is defined, it can apply to inbound or outbound packets, or both. In addition, filter rules are flexible enough to specify taking an action (such as forward or drop) on those packets that match the rules, or on all packets except those that match the rules.
Basic types of filters
Each Filter profile contains up to 12 Input-Filters (which are applied to inbound packets) and 12 Output-Filters (which are applied to outbound packets). Each of those specifications can be one of the following basic types of filters:
- Generic filters
- IP filters
- IPX filters
- Route filters
Generic filters examine the byte- or bit-level contents of any packet. They specify a forwarding action based on a comparison between certain bytes or bits in a packet and a value defined in the filter. To use generic filters effectively, you need to know the contents of certain bytes in the packets you wish to filter. Protocol specifications are usually the best source of such information.
IP filters apply only to IP-related packets. They specify a forwarding action based on higher-level fields in IP packets, such as source or destination address, protocol number, and so forth. They operate on logical information, which is relatively easy to obtain.
IPX filters apply only to NetWare packets. They specify a forwarding action based on higher-level fields, such as source or destination network, node, and socket numbers. Like IP filters, IPX filters operate on logical information, which is relatively easy to get.
Route filters apply only to RIP update packets. They specify whether matching routes in a RIP packet will be accepted into the routing table or denied, or accepted with an increased metric. They can also specify a source address, to take an action on all updates from that address.
What filters are for
After you have defined a packet filter, you apply it to an interface to monitor packets crossing that interface. You can apply the filter as one of the following:
- A data filter, to define which packets can or cannot cross the interface.
- A call filter, to define which packets can or cannot bring up a connection or reset the idle-timer for an established connection (WAN interfaces only).
- A route filter, to define which routes affect the MAX TNT routing table.
Packets can pass through both a data filter and call filter on a WAN interface. When both a data filter and call filter are applied to the same interface, the data filter is applied first.
Data filters for dropping or forwarding certain packets
Data filters are commonly used for security, but they can apply to any purpose that requires the MAX TNT to drop or forward specific packets. The focus is typically to keep out traffic that you don't want on your LAN. For example, you can use data filters to drop packets addressed to particular hosts or to prevent broadcasts from going across the WAN. You can also use data filters to allow users to access only specific devices across the WAN.
When you apply a data filter, its forwarding action (forward or drop) affects the actual data stream by preventing certain packets from reaching the Ethernet from the WAN, or vice versa. Data filters do not affect the idle timer, and a data filter applied to a Connection profile does not affect the answering process.
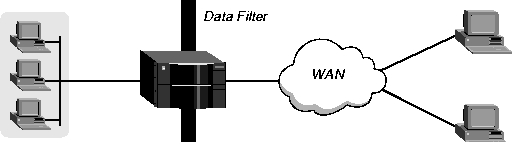
Figure 9-1. Data filters drop or forward certain packets
Call filters for managing connections
Call filters prevent unnecessary connections and help the MAX TNT distinguish active traffic from "noise." By default, any traffic to a remote site triggers a call, and any traffic across an active connection resets the connection's idle timer.
When you apply a call filter, its forwarding action (forward or drop) does not affect which packets are sent across an active connection. The forwarding action of a call filter determines which packets can either initiate a connection or reset a session's timer. When a session's idle-timer expires, the session is terminated. The Idle-Timer is set to 120 seconds by default, so if a connection is inactive for two minutes, the MAX TNT terminates the connection.
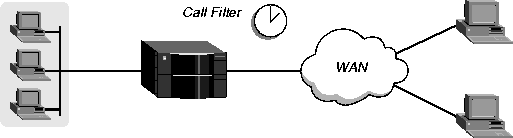
Figure 9-2. Call filters prevent certain packets from resetting the timer
Route filters for managing RIP updates
Route filters specify which routes in RIP update packets will be allowed to affect the routing table. They can also be used to increase the metric assigned to a route before adding it to the routing table.
When a route filter is applied to an IP interface, the MAX TNT monitors RIP packets on that interface and takes a specified action when a route matches the filter rules. Depending on how the filter is defined, it can apply to inbound or outbound RIP packets, or both. Route filters are supported only in Filter profiles defined locally in the command-line interface, not in filters defined in RADIUS.
Note: Route filters do not stop RIP update packets from being forwarded. Their action
determines whether matching routes are added the routing table or not.
How filters work
A Filter profile can specify up to 12 Input-Filter and Output-Filter rules. Each rule has its own forwarding action-forward or drop. The rules are applied in sequence, and a match occurs at the first successful comparison between a rule and the packet being examined. When a comparison succeeds, the filtering process stops and the forwarding action in that rule is applied to the packet. For route filters, the forwarding action has no effect, but another type of action in the rule is applied to the packet when a comparison succeeds.
If no comparison succeeds, the packet does not match this filter. However, this does not mean that the packet is forwarded. When no filter is in use, the MAX TNT forwards all packets, but once you apply a filter to an interface, this default is reversed. For security purposes, the unit does not automatically forward non-matching packets. It requires a rule that explicitly allows those packets to pass. For a sample Input-Filter that forwards packets that did not match a previous rule, see Example of an IP filter to prevent IP address spoofing.
Note: For a call filter to prevent an interface from remaining active unnecessarily, you must
define rules for both input and output packets. Otherwise, if only input rules are defined, output
packets will keep a connection active, or vice versa.
Generic filters
In a generic filter, all parameter settings in a rule work together to specify a location in a packet and a number to be compared to that location. The Comp-Neq parameter specifies whether a comparison succeeds when the contents of the packet equal the specified number or when they do not equal the number.
IP filters
In an IP filter, each rule includes a set of comparisons that are made in a defined order. When a comparison fails, the packet is allowed to go on to the next comparison. When a comparison succeeds, the filtering process stops and the forwarding action in the rule is applied to the packet. The IP filter tests proceed in the following order:
- Apply the Source-Address-Mask to the Source-Address value and compare the result to
the source address of the packet. If they are not equal, the comparison fails.
- Apply the Dest-Address-Mask to the Dest-Address value and compare the result to the
destination address in the packet. If they are not equal, the comparison fails.
- If the Protocol parameter is zero (which matches any protocol), the comparison succeeds.
If it is non-zero and not equal to the protocol field in the packet, the comparison fails.
- If the Src-Port-Cmp parameter is not set to None, compare the Source-Port number to the
source port number of the packet. If they do not match as specified in the Src-Port-Cmp
parameter, the comparison fails.
- If the Dst-Port-Cmp parameter is not set to None, compare the Dest-Port number to the
destination port number of the packet. If they do not match as specified in the Dst-Port-
Cmp parameter, the comparison fails.
- If TCP-Estab is Yes and the protocol number is 6, the comparison succeeds.
IPX filters
In an IPX filter, each rule includes a set of comparisons that are made in a defined order. When a comparison fails, the packet is allowed to go on to the next comparison. When a comparison succeeds, the filtering process stops and the forwarding action in the rule is applied to the packet. The IPX filter tests proceed in the following order:
- Compare the Src-Net-Address number to the source network number of the packet. If they
are not equal, the comparison fails.
- Compare the Dest-Net-Address number to the destination network number in the packet.
If they are not equal, the comparison fails.
- Compare the Src-Node-Address number to the source node number of the packet. If they
are not equal, the comparison fails.
- Compare the Dest-Node-Address number to the destination node number in the packet. If
they are not equal, the comparison fails.
- If the Src-Socket-Cmp parameter is not set to None, compare the Src-Socket number to
the source socket number of the packet. If they do not match as specified in the Src-
Socket-Cmp parameter, the comparison fails.
- If the Dst-Socket-Cmp parameter is not set to None, compare the Dest-Socket number to
the destination socket number of the packet. If they do not match as specified in the Dst-
Socket-Cmp parameter, the comparison fails.
Route filters
In a Route filter, each rule includes a set of comparisons that are made in a defined order. When a comparison fails, the packet is allowed to go on to the next comparison. When a comparison succeeds, the filtering process stops and the action in the rule is applied to the packet. The Route filter tests proceed in the following order:
- Apply the Source-Address-Mask to the Source-Address value and compare the result to
the source address of the packet. If they are not equal, the comparison fails.
- Apply the Route-Mask to the Route-Address value and compare the result to the routes in
the packet. If there is no match, the comparison fails.
If one of the preceding tests succeed, the following actions are performed:
- If Action is set to Add, increase the metric field of the matching routes by the Add-Metric value and then add them to the routing table.
- If Action is set to Accept, add the matching routes to the routing table.
- If Action is set to Deny, reject the matching routes (do not add them to the routing table).
Introduction to Filter profiles
Filter profiles contain parameters that set the rules describing packets and what to do when those packets are encountered. They contain separate subprofiles for the different types of filters. The settings in each subprofile are described in separate sections later in this chapter. This section describes the higher-level parameters that are common to all filter types.
Following are the relevant parameters, shown with their default settings:
FILTER filter-name
filter-name* = filter-name
input-filters
input-filters[1]-input-filters[12]
valid-entry = no
forward = no
type = generic-filter
output-filters
output-filters[1]-output-filters[12]
valid-entry = no
forward = no
type = generic-filter
Table 9-1. Basic elements of a Filter profile
Element
|
Usage
|
|---|
|
Filter-Name
|
You must assign each filter a name, so that it can be applied by name to an interface. The name you assign becomes the Filter profile's index.
|
|
Input-Filters (1-12)
|
Each filter can contain up to 12 Input-Filter specifications, which are defined individually and applied in order (1-12) to the inbound packet stream.
|
|
Output-Filters (1-12)
|
Each filter can contain up to 12 Output-Filter specifications, which are defined individually and applied in order (1-12) to the outbound packet stream.
|
|
Valid-Entry
|
Enables or disables the filter specification. When it is set to No (the default), that specification is skipped when filtering the data stream. Set it to Yes for each defined filter you intend to use.
|
|
Forward
|
Specifies the forwarding action for the filter. When no filters are in use, the MAX TNT forwards all packets by default. When a filter is in use, the default is to discard matching packets (forward = no). Note that for route filters, the forwarding action has no effect.
|
|
Type
|
Type can be set to Generic-Filter (the default), IP-Filter, IPX-Filter, or Route-Filter. Only the parameters in the corresponding subprofile will be applicable.
|
Defining generic filters
Generic filters can match any packet, regardless of its protocol type or header fields. They use the following parameters, which are shown with their default values:
FILTER filter-name
filter-name* = filter-name
input-filters
input-filters[1]-input-filters[12]
valid-entry = no
forward = no
type = generic-filter
gen-filter
offset = 0
len = 0
more = no
comp-neq = no
mask = 00:00:00:00:00:00:00:00:00:00:00:00
value = 00:00:00:00:00:00:00:00:00:00:00:00
output-filters
output-filters[1]-output-filters[12]
valid-entry = no
forward = no
type = generic-filter
gen-filter
offset = 0
len = 0
more = no
comp-neq = no
mask = 00:00:00:00:00:00:00:00:00:00:00:00
value = 00:00:00:00:00:00:00:00:00:00:00:00
Generic filter rules
The Gen-Filter subprofile contains parameters for defining generic filter rules. The following subsections explain how these rules work. (For details, see the MAX TNT Reference Guide.)
Specifying the offset to the bytes to be examined
The Offset specifies a byte-offset from the start of a frame to the data in the packet to be tested against this filter. For example, with the following filter specification:
gen-filter
offset = 2
len = 8
more = no
comp-neq = no
mask = 0f:ff:ff:ff:00:00:00:f0:00:00:00:00
value = 07:fe:45:70:00:00:00:90:00:00:00:00
and the following packet contents:
2A 31 97 FE 45 70 12 22 33 99 B4 80 75
The first two byes in the packet (2A and 31) are ignored due to the two-byte Offset.
Specifying the number of bytes to test
The Len parameter specifies the number of bytes to test in a packet, starting at the specified offset. The MAX TNT compares the contents of those bytes to the Value specified in the filter's Value parameter. For example, with the following filter specification:
gen-filter
offset = 2
len = 8
more = no
comp-neq = no
mask = 0f:ff:ff:ff:00:00:00:f0:00:00:00:00
value = 07:fe:45:70:00:00:00:90:00:00:00:00
and the following packet contents:
2A 31 97 FE 45 70 12 22 33 99 B4 80 75
The filter applies the mask only to the eight bytes following the two-byte offset.
Linking to the next Input-Filter or Output-Filter in sequence
The More parameter specifies whether the MAX TNT includes the next rule before determining whether the packet matches the filter. If More is set to Yes, the current rule is linked to the one immediately following it, so the filter can examine multiple noncontiguous bytes within a packet before the forwarding decision is made. The match occurs only if both rules are matched.
The next rule must be enabled (Valid-Entry must be set to Yes). Otherwise, the MAX TNT ignores the rule in which More is set to Yes.
Type of comparison to perform when matching the packet
The Comp-Neq (Compare-Not-Equals) parameter specifies the type of comparison to make between the specified Value and the packet's contents. If Comp-Neq is set to Yes, the comparison succeeds if the contents do not equal the specified value. For a rule that requires the packet contents to equal the specified value, leave Comp-Neq set to No.
Masking the value before comparison
Mask specifies a 12-byte mask to apply to the value specified by the Value parameter before comparing it to the packet contents at the location specified in the Offset parameter. You can set the Mask parameter to fine-tune exactly which bits you want to compare. It is assumed to the same number of octets as the Len parameter.
The MAX TNT applies the mask to the specified Value using a logical AND after the mask and Value are both translated into binary format. The mask hides the bits that appear behind each binary 0 (zero) in the mask. A mask of all ones (FF:FF:FF:FF:FF:FF:FF:FF) masks no bits, so the full specified Value must match the packet contents. For example, with the following filter specification:
gen-filter
offset = 2
len = 8
more = no
comp-neq = no
mask = 0f:ff:ff:ff:00:00:00:f0:00:00:00:00
value = 07:fe:45:70:00:00:00:90:00:00:00:00
and the following packet contents:
2A 31 97 FE 45 70 12 22 33 99 B4 80 75
The mask is applied as shown below, resulting in a Value that matches the Value.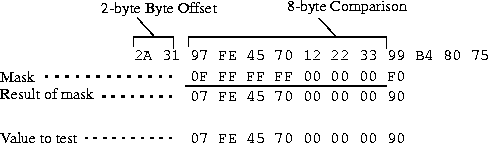
The packet matches this filter. Because the forward parameter is set to No, the packet will be dropped. The byte comparison works as follows:
- 2A and 31 are ignored due to the two-byte offset.
- 9 in the lower half of the third byte is ignored, because the mask has a 0 in its place. The 7 in the third byte matches the Value parameter's 7 in the upper half of that byte.
- F and E in the fourth byte match the fourth byte specified by the Value parameter.
- 4 and 5 in the fifth byte match the fifth byte specified by the Value parameter.
- 7 and 0 in the sixth byte match the sixth byte specified by the Value parameter.
- 12 and 22 and 33 in the seventh, eighth and ninth bytes are ignored because the mask has zeroes in those places.
- 9 in the tenth byte matches the Value parameter's 9 in the lower half of that byte. The second 9 in the upper-half of the packet's tenth byte is ignored because the mask has a 0 in its place.
The Value to match against the packet contents
The Value parameter specifies a hexadecimal number to be compared to specific bits contained in packets after the Offset, Length, and Mask calculations have been applied. After you have entered the number, the system enters a colon at the byte boundaries.
Example of a generic call filter
The following example shows how to define a generic call filter. The filter's purpose is to prevent inbound packets from resetting the session-timer. In the Input-Filter rule that follows, the default values are left in the Gen-Filter subprofile, so all packets are matched, and the forwarding action is left at the default No:
admin> new filter out-only
FILTER/out-only read
admin> list input 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
In the Output-Filter rule that follows, the default values again match all packets, but the forwarding action is set to Yes. So the filter does not prevent outbound packets from resetting the timer or placing a call.
admin> list .. .. output 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> write
FILTER/out-only written
Defining IP filters
The IP-Filter subprofile contains the following parameters, which are shown with their default values:
FILTER filter-name
filter-name* = filter-name
input-filters
input-filters[1]-input-filters[12]
valid-entry = no
forward = no
type = ip-filter
ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
output-filters
output-filters[1]-output-filters[12]
valid-entry = no
forward = no
type = ip-filter
ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
IP filter rules
IP filter rules affect only IP and related packets. The following subsections provide background information about how the IP filter parameters work. (For details, see the MAX TNT Reference Guide.)
Filtering on the protocol number field in IP packets
A protocol number of zero matches all protocols. If you specify a non-zero number, the MAX TNT compares it to the Protocol field in packets. Common protocols are listed below, but protocol numbers are not limited to this list. For a complete list, see RFC 1700, Assigned Numbers, by Reynolds, J. and Postel, J., October 1994.
- 1-ICMP
- 2-IGMP
- 4-IP
- 6-TCP
- 8-EGP
- 17-UDP
- 37-DDP
- 42-SDRP
- 45-IDRP
- 47-GRE
- 88-IGRP
- 89-OSPF
Filtering by source address
To filter packets on the basis of their source IP address, use the Source-Address-Mask and Source-Address parameters.
If you specify a Source-Address-Mask, the MAX TNT applies it to the Source-Address value before comparing that value to the source address in a packet. The MAX TNT translates both the Source-Address-Mask and Source-Address values into binary format and then uses a logical AND to apply the Source-Address-Mask to the Source-Address. The mask hides the portion of the Source-Address that appears behind each binary 0 (zero) in the mask. A mask of all zeros (the default) masks all bits. If the Source-Address value is also all zeros, all source addresses in packets are matched. A mask of all ones (255.255.255.255) masks no bits, so the full source address for a single host is matched.
You can use the address mask to mask out the host portion of an address, for example, or the host and subnet portion, so the rule matches the source address from any host on a given network.
Filtering by destination address
To filter packets on the basis of their destination IP address, use the Dest-Address-Mask and Dest-Address parameters.
If you specify a Dest-Address-Mask, the MAX TNT applies it to the Dest-Address value before comparing that value to the destination address in a packet. The MAX TNT translates both the Dest-Address-Mask and Dest-Address values into binary format and then uses a logical AND to apply the Dest-Address-Mask to the Dest-Address. The mask hides the portion of the Dest-Address that appears behind each binary 0 (zero) in the mask. A mask of all zeros (the default) masks all bits. If the Dest-Address value is also all zeros, all destination addresses in packets are matched. A mask of all ones (255.255.255.255) masks no bits, so the full destination address for a single host is matched.
You can use the address mask to mask out the host portion of an address, for example, or the host and subnet portion, so the rule matches the destination address from any host on a given network.
Filtering by port numbers
The Source-Port and Dest-Port parameters specify a port number to be compared with the source and destination ports in a packet. TCP and UDP port numbers are typically assigned to services. Common port assignments are listed below, but well-known ports are not limited to this list. For a complete list, see RFC 1700, Assigned Numbers, by Reynolds, J. and Postel, J., October 1994.
- 7- Echo
- 20- File Transfer [Default Data]
- 21-File Transfer [Control]
- 23vTelnet
- 25-Simple Mail Transfer
- 49-Login
- 53-Domain Name Server
- 65-TACACS-Database Service
- 67- Bootstrap Protocol Server
- 69-Trivial File Transfer
- 79-Finger
- 80-World Wide Web HTTP
- 137-NETBIOS Name Service
- 161-SNMP
- 162-SNMPTRAP
- 179-Border Gateway Protocol
- 201-AppleTalk Routing Maintenance
- 202-AppleTalk Name Binding
- 204-AppleTalk Echo
- 206-AppleTalk Zone Information
- 213-IPX
Note: For security purposes, you should filter all services that are not required from outside
your domain. UDP-based services are particularly vulnerable to certain types of security
attacks.
A port number of zero matches nothing. The Src-Port-Cmp and Dst-Port-Cmp parameters specify how the source and destination port numbers, respectively, will be compared to packet contents. If set to None, no comparison is made. You can specify that the filter matches the packet if the packet's port number is Less (less than), Eql (equal to), Gtr (greater than), or Neq (not equal to) the port number specified in the filter.
Filtering only established TCP sessions
Tcp-Estab can be used to restrict the filter to packets in an established TCP session. You can use it only if the protocol number has been set to 6 (TCP).
Example of an IP filter to prevent IP address spoofing
IP-address spoofing occurs when a remote device illegally acquires a local address and uses it to try to break through a Firewall or data filter. This section presents an example of a data filter that prevents IP-address spoofing. The filter first defines two Input-Filters that drop packets whose source address is on the local IP network or is the loopback address (127.0.0.0). In effect, these rules say: "If you see an inbound packet with one of these source addresses, drop the packet." The third Input-Filter accepts all remaining source addresses (by specifying a source address of 0.0.0.0) and forwards them to the local network.
This example uses a local IP network address of 192.100.50.128, with a subnet mask of 255.255.255.192. These addresses are just examples.
Note: If you apply this filter to the Ethernet interface, the MAX TNT drops IP packets it
receives from local LAN, and you will not be able to Telnet to the unit.
The following procedure defines the filter:
- Create the Filter, activate the first Input-Filter, and set the Type to IP-Filter. (Leave
Forward set to No.)
admin> new filter ip-spoof
FILTER/ip-spoof read
admin> list input 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set type = ip-filter
- List the IP-Filter subprofile, and use Set commands to specify the source mask and address
for the local network. If an incoming packet has the local address, the MAX TNT drops it
instead of forwarding it to the Ethernet, because Forward is set to No.
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set source-address-mask = 255.255.255.192
admin> set source-address = 192.100.50.128
- Activate Input-Filter 2 and set the Type to IP-Filter. (Leave Forward set to No.)
admin> list .. .. 2
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set type = ip-filter
- List the IP-Filter subprofile, and use Set commands to specify the loopback source
address. If an incoming packet has the loopback address, the MAX TNT drops it instead
of forwarding it to the Ethernet, because Forward is set to No.
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set source-address-mask = 255.0.0.0
admin> set source-address = 127.0.0.0
- Activate Input-Filter 3, set Forward to yes, and set the Type to IP-Filter:
admin> list .. .. 3
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- Leave all default values in the IP-Filter subprofile for Input-Filter 3. Because Forward is
set to Yes, the MAX TNT forwards all remaining packets (those with nonlocal source
addresses) to the Ethernet.
- Activate Output-Filter 1, set Forward to Yes, and set the Type to IP-Filter:
admin> list .. .. .. output 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- List the IP-Filter subprofile, and use Set commands to specify the source mask and address
for the local network. (Packets originating on the local network should be forwarded
across the WAN.)
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set source-address-mask = 255.255.255.192
admin> set source-address = 192.100.50.128
- Write the Filter profile:
admin> write
filter/ip-spoof written
Example of an IP filter for more complex security issues
This section illustrates some of the issues you might need to consider when writing your own IP filters. However, the sample filter presented here does not address the fine points of network security. You might want to use this filter as a starting point and augment it to address your security requirements.
In this example, the local network supports a Web server, and the administrator needs to carry out the following tasks:
- Provide dial-in access to the server's IP address
- Restrict dial-in traffic to all other hosts on the local network
However, many local IP hosts need to dial out to the Internet and use IP-based applications such as Telnet or FTP, so their response packets need to be directed appropriately to the originating host. In this example, the Web server's IP address is 192.9.250.5. The filter will be applied in Connection profiles as a data filter.
The following procedure defines the filter:
- Create a Filter profile:
admin> new filter web-safe
FILTER/web-safe read
- Activate Input-Filter 1, set Forward to Yes, and set Type to IP-Filter:
admin> list input 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- To allow packets to reach the Web server's destination address at a destination TCP port
which can be used for Telnet or FTP, list the IP-Filter subprofile and use Set commands as
follows:
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set protocol = 6
admin> set dest-address-mask = 255.255.255.255
admin> set dest-address = 192.9.250.5
admin> set dst-port-cmp = eql
admin> set dest-port = 80
- Activate Input-Filter 2, set Forward to Yes, and set Type to IP-Filter:
admin> list .. .. 2
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- To allow inbound TCP packets that are responding to a local user's outbound Telnet
request, you can forward TCP packets whose destination port is greater than the source
port. (Telnet requests go out on port 23 and responses come back on some random port
greater than port 1023.) List the IP-Filter subprofile and use Set commands as follows:
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set protocol = 6
admin> set dst-port-cmp = gtr
admin> set dest-port = 1023
- Activate Input-Filter 3, set Forward to Yes, and set the Type to IP-Filter:
admin> list .. .. 3
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- To allow inbound RIP updates, you can specify a filter that forwards inbound UDP packets
if the destination port is greater than the source port. (For example, suppose a RIP packet
goes out as a UDP packet to destination port 520. The response to this request goes to a
random destination port greater than 1023.) List the IP-Filter subprofile and use Set
commands as follows:
admin> list ip-filter
protocol = 0
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
dest-address-mask = 0.0.0.0
dest-address = 0.0.0.0
Src-Port-Cmp = none
source-port = 0
Dst-Port-Cmp = none
dest-port = 0
tcp-estab = no
admin> set protocol = 17
admin> set dst-port-cmp = gtr
admin> set dest-port = 1023
- Activate Input-Filter 4, set Forward to Yes, and set Type to IP-Filter:
admin> list .. .. 4
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
admin> set valid = yes
admin> set forward = yes
admin> set type = ip-filter
- Leave all default values in the IP-Filter subprofile for Input-Filter 4. This allows
unrestricted Pings and Traceroutes. ICMP does not use ports like TCP and UDP, so a port
comparison is unnecessary.
- Write the Filter profile:
admin> write
FILTER/web-safe written
Defining IPX filters
The IPX-Filter subprofile contains the following parameters, which are shown with their default values:
FILTER filter-name
filter-name* = filter-name
input-filters
input-filters[1]-input-filters[12]
valid-entry = no
forward = no
type = ipx-filter
ipx-filter
src-net-address = 00:00:00:00
dest-net-address = 00:00:00:00
src-node-address = 00:00:00:00:00:00
dest-node-address = 00:00:00:00:00:00
src-socket = 00:00
src-socket-cmp = none
dest-socket = 0
dst-socket-cmp = none
output-filters
output-filters[1]-output-filters[12]
valid-entry = no
forward = no
type = ipx-filter
ipx-filter
src-net-address = 00:00:00:00
dest-net-address = 00:00:00:00
src-node-address = 00:00:00:00:00:00
dest-node-address = 00:00:00:00:00:00
src-socket = 00:00
src-socket-cmp = none
dest-socket = 0
dst-socket-cmp = none
IPX filter rules
IPX filter rules affect only NetWare packets, and their fundamental focus is to identify networks, hosts, or services. The following subsections provide background information about how the IPX filter parameters work. (For details, see the MAX TNT Reference Guide.)
Filtering on source or destination address
The network address and node address parameters are designed to work together to specify a source or destination NetWare server. A full IPX network address uses the following format:
<network-number>:<node-number>
The Src-Net-Address and Dest-Net-Address parameters specify the network-number portion of the address. The network number is a unique 8-byte hexadecimal number that is common to all hosts on a particular LAN. NetWare servers have an internal network number that is the destination network address for file read/write requests. (If you are not familiar with internal network numbers, see your NetWare documentation for details.)
The Src-Node-Address and Dest-Node-Address parameters specify the node-number portion of the address. The node number is a 12-byte hexadecimal number that is unique to each node on a LAN. Each filter that specifies an IPX network number should also specify the corresponding node number. (For example, if you specify the Src-Net-Address in a filter, you should also specify the Src-Node-Address.)
Typically, a NetWare server address has the node number 1 (00:00:00:00:00:01) on the server's internal network. A node number of all 1s (FF:FF:FF:FF:FF:FF) matches all nodes on a LAN.
Source or destination socket number and the method of comparison
NetWare servers use a particular socket number for each service. For example, NetWare file service typically uses socket 0451 (04:51). Some services use dynamic socket numbers, which may change each time they load. A socket number of all 1s (FF:FF) matches any socket on the specified server.
When you specify a NetWare socket number, you must also indicate how to compare the socket number in a packet to the specification in the filter. The Src-Socket-Cmp parameter specifies the method of comparison for the source socket number. You can specify that the filter matches the packet if the packet's source socket number is Less (less than), Eql (equal to), Gtr (greater than), or Neq (not equal to) the source socket number specified in the filter.
The Dst-Socket-Cmp parameter specifies the method of comparison for the destination socket number. You can specify that the filter matches the packet if the packet's destination socket number is Less (less than), Eql (equal to), Gtr (greater than), or Neq (not equal to) the destination socket number specified in the filter.
Example of an outbound IPX filter
When the following sample IPX filter is applied as a data filter to a WAN interface, it causes the MAX TNT to drop all outbound IPX packets with the destination IPX network 00003823, regardless of the destination IPX node or socket number in the packets. All other packets are forwarded.
admin> new filter dstipx
FILTER/dstipx read
admin> list output 1
valid-entry = no
forward = no
Type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0 none }
ipx-filter = { 00:00:00:00 00:00:00:00 00:00:00:00:00:00 00:00:00:00:0+
admin> set type = ipx-filter
admin> set ipx dest-net-address = 00003823
admin> set ipx dest-node-address = ffffffffffff
admin> list .. 2
valid-entry = no
forward = no
Type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0 none }
ipx-filter = { 00:00:00:00 00:00:00:00 00:00:00:00:00:00 00:00:00:00:0+
admin> set forward = yes
admin> write
FILTER/dstipx read
Example of an inbound IPX filter
When the following sample IPX filter is applied as a data filter to a WAN interface, it causes the MAX TNT to drop all inbound IPX packets from a specific source. In this example, the filter causes the MAX TNT to drop packets from the source IPX network address 00000005:00abcde12345 and the source socket number of 4002. All other packets are forwarded.
admin> new filter srcipx
FILTER/srcipx read
admin> list input 1
valid-entry = no
forward = no
Type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0 none }
ipx-filter = { 00:00:00:00 00:00:00:00 00:00:00:00:00:00 00:00:00:00:0+
admin> set type = ipx-filter
admin> set ipx src-net = 00000005
admin> set ipx src-node = 00abcde12345
admin> set ipx src-socket = 4002
admin> set ipx src-socket-cmp = eql
admin> list .. 2
valid-entry = no
forward = no
Type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0 none }
ipx-filter = { 00:00:00:00 00:00:00:00 00:00:00:00:00:00 00:00:00:00:0+
admin> set forward = yes
admin> write
FILTER/srcipx read
Defining route filters
The Route-Filter subprofile contains the following parameters, which are shown with their default values:
FILTER filter-name
filter-name* = ""
input-filters
input-filters[1]-input-filters[12]
valid-entry = no
forward = no
type = route-filter
route-filter
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
route-mask = 0.0.0.0
route-address = 0.0.0.0
add-metric = 0
action = none
output-filters
output-filters[1]-output-filters[12]
valid-entry = no
forward = no
type = route-filter
route-filter
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
route-mask = 0.0.0.0
route-address = 0.0.0.0
add-metric = 0
action = none
Note: For route filters, the forwarding action has no effect.
Route filter rules
Route filter rules affect only RIP packets. The following subsections provide background information about how the route filter parameters work. (For details, see the MAX TNT Reference Guide.)
Source address and address mask
The Source-Address-Mask and Source-Address parameters specify the source of the route. These parameters have meaning only in input filters. A source address of zero with a mask of zero matches any source.
Route address and mask
Route-Mask and Route-Address specify the destination of the route. When a route in a RIP packet matches this specification, the MAX TNT takes the specified action.
Specifying the action to take
The Action parameter specifies what action to take on a route that matches the specified Route-Mask and Route-Address. These are the possible actions:
- None (the default)
- Accept (accept the route by allowing it to affect the routing table).
- Deny (deny the route by not allowing it to affect the routing table).
- Add (add the Value set in the add-Metric parameter to the route Metric and accept the route).
Example of a filter that excludes a route
In the following example, the defined Input-Filters accept all inbound RIP packets except those with a destination of 90.0.0.0. Following are the commands entered to define the filter, and the system's responses:
admin> new filter route-test
FILTER/route-test read
admin> list input 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 255.0.0.0 90.0.0.0 0 deny }
admin> set valid = yes
admin> set type = route-filter
admin> list route
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
route-mask = 255.0.0.0
route-address = 90.0.0.0
add-metric = 0
action = none
admin> set route-mask = 255.0.0.0
admin> set route-address = 90.0.0.0
admin> set action = deny
admin> list .. .. 2
admin> set valid = yes
admin> set type = route-filter
admin> set route action = accept
admin> write
FILTER/route-test written
Note: In this sample route filter, any route that matches filter 1 is rejected, and all other routes
are accepted (because they match filter 2).
Example of a filter that configures a route's metric
In the following example, an Output-Filter identifies the route 11.0.0.0 in outbound RIP packets and assigns a high metric to that route. Following are the commands entered and the system's responses:
admin> new filter metrics
FILTER/metrics read
admin> list output 1
valid-entry = no
forward = no
type = generic-filter
gen-filter = { 0 0 no no 00:00:00:00:00:00:00:00:00:00:00:00 00:00:00:0+
ip-filter = { 0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 none 0 none 0 no }
route-filter = { 0.0.0.0 0.0.0.0 255.0.0.0 90.0.0.0 0 deny }
admin> set valid = yes
admin> set type = route-filter
admin> list route
source-address-mask = 0.0.0.0
source-address = 0.0.0.0
route-mask = 255.0.0.0
route-address = 90.0.0.0
add-metric = 0
action = none
admin> set route-mask = 255.0.0.0
admin> set route-address = 11.0.0.0
admin> set add-metric = 7
admin> set action = add
admin> write
FILTER/metrics written
Applying a filter to an interface
When you apply a filter to an interface, it causes the MAX TNT to examine packets on the interface. Following are the parameters related to applying a filter, shown with their default settings:
ANSWER-DEFAULTS
session-info
call-filter = ""
data-filter = ""
filter-persistence = no
CONNECTION station
session-options
call-filter = ""
data-filter = ""
filter-persistence = no
ip-options
route-filter = ""
ETHERNET {shelf-N slot-N N }
filter-name= ""
IP-INTERFACE { {shelf-N slot-N N } N}
route-filter = ""
For information about each parameter, see the MAX TNT Reference Guide. For information about the effect of applying a data filter, call filter, or route filter, see What filters are for.
How the system uses Answer-Defaults profile settings
If the MAX TNT uses a local Connection profile for authentication, it does not use filters applied in the Answer-Defaults Session-Info subprofile.
If the MAX TNT relies on RADIUS for authentication, and the caller's RADIUS profile applies a data filter or call filter (or both), those filters are applied to each incoming packet, and the MAX TNT does not use filters applied in the Answer-Defaults Session-Info subprofile.
If the MAX TNT relies on RADIUS for authentication, the caller's RADIUS profile does not apply a data filter or call filter, and the Use-Answer-For-All-Defaults parameter is set to Yes in the Answer-Default profile, filters applied in the Answer-Defaults Session-Info subprofile are applied to each incoming packet.
How filter persistence affects filters
Filter persistence is needed to allow Secure Access Firewalls to persist across connection state changes, but it is not needed for filters. If you do set it for a filter, the filter persists across connection state changes. For more information about persistence, see Appendix C, Secure Access Firewalls.
Applying a data filter to a WAN or LAN interface
When you apply a filter to a WAN interface, it takes effect when the connection is brought up. If both a data filter and call filter are applied, the data filter is applied first, so only those packets that pass the data filter reach the call filter.
Following is an example of applying a data filter:
admin> read conn tlynch
CONNECTION/tlynch read
admin> list session
call-filter = ""
data-filter = ""
filter-persistence = no
idle-timer = 120
ts-idle-mode = no-idle
ts-idle-timer = 120
admin> set data-filter = ip-spoof
admin> write
CONNECTION/tlynch written
Ethernet interfaces are connected routes, so call filters are not applicable. However, you can apply a data filter that affects which packets are allowed to reach the Ethernet or leave the Ethernet for another interface. A filter applied to an Ethernet interface takes effect immediately. If you change the Filter profile definition, the changes apply as soon as you save the Filter profile.
Note: Use caution when applying a filter to the Ethernet interface. You could inadvertently
render the MAX TNT inaccessible from the local LAN.
Following is an example of a procedure that applies a filter to a local network interface:
admin> dir ether
8 12/11/1996 15:58:08 { shelf-1 controller 1 }
16 12/18/1996 16:17:17 { shelf-1 Slot-12 1 }
16 12/18/1996 16:17:17 { shelf-1 Slot-12 2 }
16 12/18/1996 16:17:17 { shelf-1 Slot-12 3 }
16 12/18/1996 16:17:17 { shelf-1 Slot-12 4 }
admin> read ether {1 12 1}
ETHERNET/{ shelf-1 Slot-12 1 } read
admin> list
interface-address* = { shelf-1 slot-12 1 }
mac-address = 00:c0:7b:69:94:38
ether-if-type = utp
filter-name = ""
admin> set filter-name = web-safe
admin> write
ETHERNET/{ shelf-1 Slot-12 1 } written
Applying a call filter to a WAN interface
Following is an example of a procedure that applies a filter to a WAN connection and sets the idle timer to 20 seconds. If no packets get through the call filter in either direction for 20 seconds, the connection is torn down.
admin> read conn bob
CONNECTION/bob read
admin> list session
call-filter = ""
data-filter = ""
filter-persistence = no
idle-timer = 120
ts-idle-mode = no-idle
ts-idle-timer = 120
admin> set call-filter = out-only
admin> set idle-timer = 20
admin> write
CONNECTION/bob written
Applying a route filter to a WAN or LAN interface
Following is an example of applying a route filter named Route-Test in a Connection profile:
admin> read conn bdv
CONNECTION/bdv read
admin> set ip-options route-filter = route-test
admin> write
CONNECTION/bdv written
Following is an example of applying a route filter named Route-Test to a local network interface:
admin> read ip-interface { { 1 c 1 } 0 }
IP-INTERFACE/{ { shelf-1 controller 1 } 0 } read
admin> set route-filter = route-test
admin> write
IP-INTERFACE/{ { shelf-1 controller 1 } 0 } written
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.



