
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


Setting Up Filters
This chapter describes how to configure filters, and consists of the following sections:
Before you begin
If you plan to configure RADIUS to accept filter-change requests, you must specify settings in the Rad-Auth-Server subprofile of the External-Auth profile. For information about how to carry out this task, see Configuring the MAX TNT for RADIUS client requests.
Overview of packet filters
A packet filter contains rules that govern what the MAX TNT does when it encounters different types of packets. When you specify a packet filter in a RADIUS user profile, the MAX TNT monitors the data stream associated with that profile and takes a specified action when packet contents match the filter rules. Each filter specification directs the MAX TNT to either forward or drop packets. You can apply a filter to inbound packets, outbound packets, or both. In addition, you can specify that the MAX TNT forward or drop those packets that match the rules, or all packets except those that match the rules.
Types of packet filters
The MAX TNT supports two types of packet filters: generic and IP. The sections that follow describe each type of filter.
Generic filters
A generic filter examines the byte- or bit-level contents of a packet. It focuses on certain bytes or bits and compare them with a value defined in the filter. To use generic filters effectively, you need to know the contents of certain bytes in the packets you wish to filter. Protocol specifications are usually the best source of such information.
IP filters
An IP filter examines higher level fields specific to IP packets. It focuses on known fields, such as source or destination address, protocol number, and so forth. An IP filter operates on logical information that is relatively easy to obtain.
Ways to apply packet filters
You can apply a generic or IP filter as either a data filter of a call filter.
Data filters for dropping or forwarding certain packets
A data filter defines which packets the MAX TNT can transmit on a connection. Many sites use data filters for security purposes, but you can apply data filters to any purpose that requires the MAX TNT to drop or forward only specific packets. For example, you can use data filters to drop packets addressed to particular hosts or to prevent broadcasts from going across the WAN. You can also use data filters to allow users to access only specific devices across the WAN.
When you apply a data filter, its forward or drop action affects the actual data stream by preventing certain packets from reaching the Ethernet from the WAN, or vice versa. Figure 11-1 illustrates the concept.
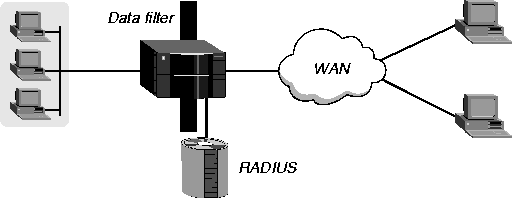
Figure 11-1. Data filters can drop or forward certain packets
Data filters do not affect the idle timer, and a data filter applied to a RADIUS user profile does not affect the answering process.
Call filters for managing connections
A call filter defines which packets can or cannot bring up a connection or reset the idle timer for an established link. Figure 11-2 shows how a call filter is different from the data filter illustrated in Figure 11-2.
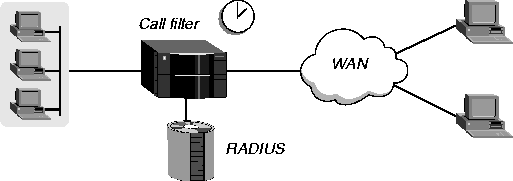
Figure 11-2. Call filters can prevent certain packets from resetting the timer
A call filter prevents unnecessary connections and helps the MAX TNT distinguish active traffic from noise. By default, any traffic to a remote site triggers a call, and any traffic across an active connection resets the connection's idle timer.
When you apply a call filter, its forwarding action does not affect which packets are sent across an active connection. The forwarding action of a call filter determines which packets can initiate a connection or reset a session's timer. When a session's idle timer expires, the MAX TNT terminates the session. The idle timer is set to 120 seconds by default, so if a connection is inactive for two minutes, the MAX TNT terminates the connection.
How packet filters work
You can specify several filters in a RADIUS user profile. Filter entries apply on a first-match basis. Therefore, the order in which you specify filter entries is significant. When you define a filter in a RADIUS user profile, it applies to data the user sends or receives. If you make changes to a filter, the changes do not take effect until a call uses that profile.
A match occurs at the first successful comparison between a filter and the packet being examined. When a comparison succeeds, the filtering process stops and the MAX TNT applies the forward or drop action to the packet.
If no comparisons succeed, the packet does not match the filter, and the MAX TNT does not forward the packet. When no filter is in use, the MAX TNT forwards all packets. However, once you apply a filter to a connection, this default is reversed. For security purposes, the MAX TNT does not automatically forward nonmatching packets. It requires a rule that explicitly allows those packets to pass.
In a generic filter, all settings work together to specify a location in a packet and a number that the MAX TNT compares to the value in that location. In an IP filter, the MAX TNT makes a set of distinct comparisons in a defined order. When a comparison fails, the packet goes on to the next comparison. When a comparison succeeds, the filtering process stops and the MAX TNT applies the forward or drop action to the packet.
The IP filter tests proceed in the following order:
- Compare the source address specified by the filter to the source address of the packet. If
they are not equal, the comparison fails.
- Compare the destination address specified by the filter to the destination address in the
packet. If they are not equal, the comparison fails.
- If the protocol specified by the filter is zero (which matches any protocol), the comparison
succeeds. If it is nonzero and not equal to the protocol field in the packet, the comparison
fails.
- If the source port of the packet does not match the source port specified by the filter, the
comparison fails.
- If the destination port of the packet does not match the destination port specified by the
filter, the comparison fails.
- If the filter specifies a match only if a TCP session is already established, and a TCP
session is up, the comparison succeeds.
Overview of filter configuration tasks
When you set up filters, you can:
Configuring an IP filter
Use the following format for an IP data-filter entry:
Ascend-Data-Filter="ip dir action [dstip dest_ipaddr\subnet_mask]
[srcip src_ipaddr\subnet_mask] [proto [dstport cmp value]
[srcport cmp value] [est]]"
Note: A filter definition cannot contain newlines. The syntax is shown here on multiple lines
for printing purposes only.
Use the following format for an IP call-filter entry:
Ascend-Call-Filter="ip dir action [dstip dest_ipaddr\subnet_mask]
[srcip src_ipaddr\subnet_mask] [proto [dstport cmp value]
[srcport cmp value] [est]]"
Table 11-1 describes each element of the syntax.
Table 11-1. IP filter syntax elements
Keyword or argument
|
Description
|
|---|
|
ip
|
Specifies an IP filter.
|
|
dir
|
Specifies filter direction. You can specify in (to filter packets coming into the MAX TNT) or out (to filter packets going out of the MAX TNT).
|
|
action
|
Specifies the action the MAX TNT should take with a packet that matches the filter. You can specify either forward or drop.
|
dstip dest_ipaddr
\subnet_mask
|
The keyword dstip enables destination-IP-address filtering.
The filter applies to packets whose destination address matches the value of dest_ipaddr. If a subnet mask portion of the address is present, the MAX TNT compares only the masked bits. If you set dest_ipaddr to 0.0.0.0, or if this keyword and its IP address specification are not present, the filter matches all IP packets.
|
srcip src_ipaddr
\subnet_mask
|
The keyword srcip enables source-IP-address filtering.
The filter applies to packets whose source address matches the value of src_ipaddr. If a subnet mask portion of the address is present, the MAX TNT compares only the masked bits. If you set src_ipaddr to 0.0.0.0, or if this keyword and its specification are not present, the filter matches all IP packets.
|
|
proto
|
Specifies a protocol specified as a name or a number.
The filter applies to packets whose protocol field matches this value.The supported names and numbers are icmp (1), tcp (6), udp (17), and ospf (89). If you set proto to 0 (zero), the filter matches any protocol.
|
|
dstport cmp value
|
The keyword dstport enables destination-port filtering. This argument is valid only when the protocol is tcp (6) or udp (17). If you do not specify a destination port, the filter matches any port.
The cmp argument defines how to compare the specified value to the actual destination port. It can have the value <, =, >, or !=.
value can be a number or a name. Supported names and numbers are ftp-data (20), ftp (21), telnet (23), smtp (25), nameserver (42), domain (53), tftp (69), gopher (70), finger (79), www (80), kerberos (88), hostname (101), nntp (119), ntp (123), exec (512), login (513), cmd (514), and talk (517).
|
|
srcport cmp value
|
The keyword srcport enables source-port filtering. It is valid only when the protocol is tcp (6) or udp (17). If you do not specify a source port, the filter matches any port.
The cmp argument defines how to compare the specified value to the actual source port. It can have the value <, =, >, or !=.
value can be a number or a name. Supported names and numbers are ftp-data (20), ftp (21), telnet (23), smtp (25), nameserver (42), domain (53), tftp (69), gopher (70), finger (79), www (80), kerberos (88), hostname (101), nntp (119), ntp (123), exec (512), login (513), cmd (514), and talk (517).
|
|
est
|
If you set this argument to 1, the filter matches a packet only if a TCP session is already established. It is valid only when the proto specification is tcp (6).
|
Example of configuring data filters for preventing IP address spoofing
IP address spoofing occurs when a remote device illegally acquires a local address to break through a firewall. In Figure 11-3, each of the dial-in users across the WAN has a RADIUS user profile. 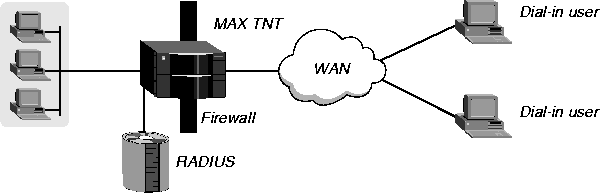
Figure 11-3. Data filters for preventing IP address spoofing
The following example show you how to define data filters to prevent break-ins that use address spoofing. In each RADIUS user profile for a dial-in user across the WAN, enter the data filters in the order specified below. Proceed as follows:
- Define a data filter that drops incoming packets whose source address is on the local IP
network (200.100.50.128):
Ascend-Data-Filter="ip in drop srcip 200.100.50.128"
Because action is set to drop, if an incoming packet has the local address, the MAX TNT does not forward it.
- Define a data filter that drops packets whose source address is the loopback address
(127.0.0.0):
Ascend-Data-Filter="ip in drop srcip 127.0.0.0"
- Define a data filter that specifies every other source address (0.0.0.0) and indicates that the
MAX TNT should forward all other packets:
Ascend-Data-Filter="ip in forward"
- Define a data filter that specifies that the MAX TNT should forward packets originating
on the local network:
Ascend-Data-Filter="ip out forward srcip 200.100.50.128"
Example of using IP data filters to allow FTP to a specific host
In Figure 11-4, the user Emma is limited to using FTP to exchange files with the host at IP address 215.5.0.4.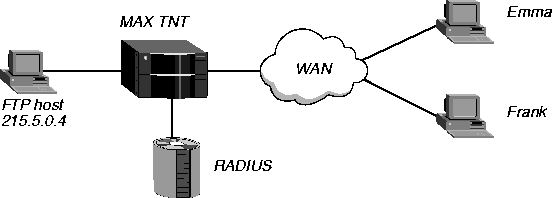
Figure 11-4. Data filters to allow FTP to a specific host
In Emma's RADIUS user profile, you must specify several IP data filters in the proper order. Proceed as follows:
- Forward incoming packets only to destination ports 20 and 21 at IP address 215.5.0.4.
Ports 20 and 21 are FTP ports. Enter the following filter specifications:
Ascend-Data-Filter="ip in forward tcp dstip 215.5.0.4 dstport=20"
Ascend-Data-Filter="ip in forward tcp dstip 215.5.0.4 dstport=21"
- Forward outgoing packets to IP address 215.5.0.4 only when the destination port is greater
than 1023. (FTP responses come back on a random port greater than 1023.) Enter the
following filter specification:
Ascend-Data-Filter="ip out forward tcp dstip 215.5.0.4 dstport >1023"
- Drop all other incoming IP packets:
Ascend-Data-Filter="ip in drop"
- Drop all other outgoing IP packets:
Ascend-Data-Filter="ip out drop"
Example of using IP data filters for complex security issues
In Figure 11-5, the local network supports a Web server at IP address 200.9.250.5.
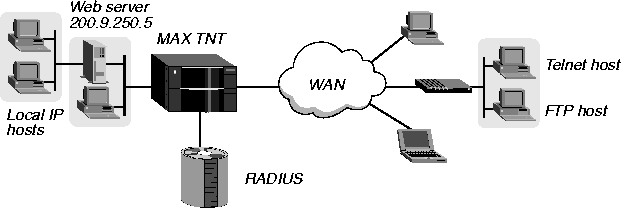
Figure 11-5. Using filters for complex security purposes
The administrator needs to carry out the following tasks:
- Provide dial-in access to the server's IP address
- Restrict dial-in traffic to all other hosts on the local network
However, many local IP hosts need to dial out to the Internet and use IP-based applications such as Telnet and FTP, so their response packets must be directed to the originating host.
In each RADIUS user profile, you must create several IP data filters in the specified order. Proceed as follows:
- Enable packets to reach the Web server's destination address at a TCP port used for Telnet
or FTP. Enter the following specification:
Ascend-Data-Filter="ip in forward dstip 200.9.250.5 tcp dstport=80"
- To allow incoming TCP packets responding to a local user's outgoing Telnet request, you
can forward TCP packets whose destination port is greater than the source port. (Telnet
requests go out on port 23, and responses come back on a random port greater than 1023.)
Enter the following specification:
Ascend-Data-Filter="ip in forward tcp dstport > 1023"
- To allow incoming RIP updates, you can forward incoming UDP packets if the destination
port is greater than the source port. Enter the following specification:
Ascend-Data-Filter="ip in forward dstip udp dstport > 1023"
- To allow unrestricted Pings and Traceroutes, enter the following specification:
Ascend-Data-Filter="ip in forward"
Configuring a generic filter
Use the following format for a generic data filter entry:
Ascend-Data-Filter="generic dir action offset mask value compare
[more]"
Note: A filter definition cannot contain newlines. The syntax is shown here on multiple lines
for printing purposes only.
Use the following format for a generic call filter entry:
Ascend-Call-Filter="generic dir action offset mask value compare
[more]"
Table 11-2 describes each element of the syntax.
Understanding generic filters
Generic filters can affect any packet, regardless of its protocol type or header fields. This section provides background information about how a generic filter specification works. The example uses a data filter for which you specify the following setting:
Ascend-Data-Filter="generic in drop 2
ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff:ff
aa:aa:03:00:00:00:80:f3:00:00:00:00"
Determining whether inbound or outbound data is examined
In this example, the filter examines inbound data only.
Specifying an offset to the bytes in a packet to be examined
The offset argument specifies a byte offset from the start of a frame to the data the MAX TNT tests against the filter. For example, suppose you specify 2 for the offset argument, and the packet contents look like the following:
2A 31 97 FE 45 70 12 22 33 99 B4 80 75
The MAX TNT ignores the first two byes in the packet (2A and 31).
Linking the filter to the next one in sequence
If the more argument is present, the MAX TNT includes the next filter before determining whether the frame matches the filter. In this case, the more argument is not present, so the MAX TNT does not include the next filter.
Masking the value before comparison
The mask argument specifies a 12-byte mask to apply to the value argument before the MAX TNT compares it to the packet contents at the specified offset. You can use the mask to specify exactly which bits you want to compare.
After the mask and value are both translated into binary format, the MAX TNT applies the mask to the specified value with a logical AND. The mask hides the bits that appear behind each binary 0 (zero) in the mask. A mask of all ones (FF:FF:FF:FF:FF:FF:FF:FF) masks no bits, so the full specified value must match the packet contents. For example, suppose you specify the following values:
offset=2
mask=0f:ff:ff:ff:00:00:00:f0:00:00:00:00
value=07:fe:45:70:00:00:00:90:00:00:00:00
and the packet contains the following data:
2A 31 97 FE 45 70 12 22 33 99 B4 80 75
The MAX TNT applies the mask as shown below, resulting in a value that matches the setting for the value argument.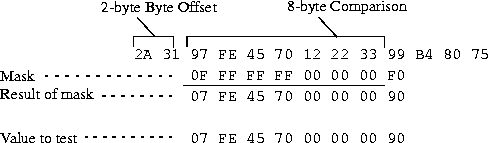
The packet matches the filter. Because the action argument is set to drop, the MAX TNT drops the packet. The byte comparison works as follows:
- The MAX TNT ignores 2A and 31 because of the two-byte offset.
- The MAX TNT ignores the 9 in the lower half of the third byte, because the mask has a 0 (zero) in its place. The 7 in the third byte matches the value argument's 7 in the upper half of that byte.
- F and E in the fourth byte match the value specified by the filter for that byte.
- 4 and 5 in the fifth byte match the value specified by the filter for that byte.
- 7 and 0 in the sixth byte match the value specified by the filter for that byte.
- The MAX TNT ignores 12, 22, and 33 in the seventh, eighth and ninth bytes, respectively, because the mask has a 0 (zero) in those places.
- 9 in the tenth byte matches the value argument's 9 in the lower half of the byte. The MAX TNT ignores the second 9 in the upper half of the packet's tenth byte because the mask has a 0 (zero) in its place.
Examples of using generic call filters
This section contains two examples of how to implement generic call filters.
Example of using a generic call filter to prevent idle timer resets
The purpose of the filter in this example is to prevent incoming packets from resetting the session's idle timer. The filter does not prevent outgoing packets from resetting the idle timer or placing a call. Enter the following specification:
Ascend-Call-Filter="generic in drop"
Example of using a generic call filter for AppleTalk traffic
In Figure 11-6, several Macintosh workstations are running Open Transport on the local LAN, and you want only IP traffic destined for the WAN to bring up a connection.
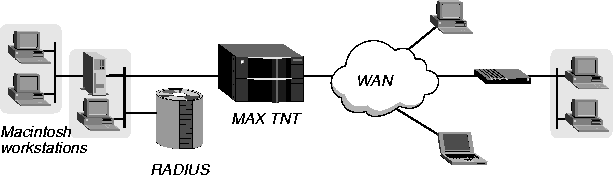
Figure 11-6. Using a generic call filter for AppleTalk traffic
To ensure that AppleTalk packets with destinations on the local LAN do not bring up a connection, you must specify several generic call filters. Configure a separate filter to carry out each of the following tasks. You must create the filters in the specified order. Proceed as follows:
- Drop AppleTalk Address Resolution Protocol (AARP) packets. Enter the following filter
specification to keep AARP packets (protocol ID 80f3) from bringing up a connection:
Ascend-Call-Filter="generic out drop 14 ffffffffffffffff aaaa0300000080f3"
- Forward non-AppleTalk traffic. AppleTalk has the protocol 809b. Enter the following filter
specification to forward all non-AppleTalk packets:
Ascend-Call-Filter="generic out forward 14 ffffffffffffffff aaaa03080007809b !="
From this point on, any additional filters deal only with AppleTalk traffic.
- Drop AppleTalk Echo Protocol (AEP) packets. Enter the following filter specification to
keep AEP packets from bringing up a connection:
Ascend-Call-Filter="generic out drop 32 ffffff0000000000 0404040000000000 !="
- Forward all traffic not destined for an AppleTalk multicast address. (AppleTalk uses a
multicast address, rather than a broadcast address.) Enter the following filter specification
to forward all packets not destined for that multicast address:
Ascend-Call-Filter="generic out forward 32 ffffffffffff0000 090007ffffff0000 !="
- Forward Name Binding Protocol (NBP) lookup packets, but only those that the Chooser
makes use of (that is, only those with a wildcard entity name). Enter the following filter
specification to forward NBP packets:
Ascend-Call-Filter="generic out forward 32 ff00fff000000000 0200022000000000 more"
The more value indicates that the MAX TNT must examine the next specification before making the decision to forward a packet. Enter the next specification to direct the MAX TNT to forward only those packets with a wildcard entity name:
Ascend-Call-Filter="generic out forward 42 ffff000000000000 013d000000000000"
Setting up filter changes
If you write a special RADIUS client program to change filters, the MAX TNT can accept RADIUS requests from clients to change a filter for a particular session, user, or IP address. The following sections describe how to configure filter-change requests.
Overview of filter-change attributes
A RADIUS Change-Filter-Request packet (code 43) contains the attributes necessary for making a filter-change request. Table 11-3 lists these attributes.
Configuring attributes for filter-change requests
The MAX TNT sends the session key and session ID in all RADIUS access requests. You can also obtain the session key, session ID, and user name through RADIUS accounting or from the accounting MIB (for systems that support SNMP accounting). If the MAX TNT assigns the IP address from a pool, RADIUS accounting or the accounting MIB can provide the address as well.
Note: The Auth-Session-Key and Auth-Attribute-Type parameters in the External-Auth
profile's Rad-Auth-Server subprofile determine the attributes the MAX TNT uses when
handling the filter-change request. For complete information about setting these parameters,
see Specifying session key parameters.
To set up a RADIUS user profile that requests a filter change, you must carry out the following steps:
- Specify the values for the User-Name and Password attributes. These attributes must
identify a user at the IP address indicated by the Auth-Client or Auth-Netmask parameters
in the External-Auth profile's Rad-Auth-Server subprofile.
- Set the Ascend-Data-Filter attribute to specify the data filter to use. You can specify this
attribute more than once.
- Set the Ascend-Call-Filter attribute to specify the call filter to use. You can specify this
attribute more than once.
Depending upon the needs of your site, you can carry out the following additional steps:
- To identify the session by IP address, set the Framed-Address attribute.
- To identify the session by its ID number, set the Acct-Session-Id attribute. The number
you specify must match the session reference number used in SNMP accounting or
RADIUS accounting.
- To identify the session by a session key, set the Ascend-Session-Svr-Key attribute.
How the MAX TNT handles filter-change requests
The MAX TNT silently discards a Change-Filter-Request packet if one of the following conditions is true:
- The packet is badly formatted.
- The client is not on the list of clients allowed to send RADIUS requests to the server.
- The authenticator field is incorrect.
- The packet contains invalid attribute values.
If RADIUS finds at least one routing session whose filters it can change, the response code is 44 (Change-Filter-Request-ACK). Otherwise, the code is 45 (Change-Filter-Request-NAK). RADIUS does not return any attributes in the response.
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.




