

Installing and Starting RADIUS
This chapter, which describes how to install and start the RADIUS daemon, consists of the following sections:
Before you begin
This section describes:
Configuring the MAX TNT
Before you install and configure RADIUS, you must carry out the following tasks at the MAX TNT configuration interface:
Overview of RADIUS installation tasks
No matter what kind of configuration exists at your site, you are required to carry out the following tasks:
Installing the RADIUS daemon
To install the RADIUS daemon, you must perform the following tasks:
clients file.
users file.
To obtain and compile the RADIUS daemon:
dictionary file is the Ascend RADIUS dictionary. It contains a list of all attributes that the RADIUS server supports. You must install the dictionary in the same directory as the Ascend RADIUS daemon. By default, the RADIUS daemon resides in the
/etc/raddb directory. The dictionary must have the same date as the Ascend RADIUS daemon. If you find a discrepancy in the dates between the daemon and the dictionary, download the latest dictionary from ftp.ascend.com, and copy it into the same directory as the daemon. Note that the RADIUS daemon reads the dictionary when it starts up. If you update the
dictionary file while the daemon is running, you must stop the daemon process and restart it to make the new attributes available. For further information about the dictionary file, see The dictionary file.
Creating and configuring the clients file
The RADIUS server does not simply authenticate incoming calls. It must also authenticate the Network Access Server (NAS) from which it receives requests. The MAX TNT is an NAS and a client of the RADIUS server. For the RADIUS daemon to respond to requests from the MAX TNT, you must create a file called clients in the /etc/raddb directory, and then specify the MAX TNT unit's name and password in the file.
clients file:
Ascend3 bXSAMpyAscend3 is the value specified by the Name parameter. The argument bXSAMpy is the password specified by the Auth-Key parameter. The name you specify must be resolvable on the IP network (through DNS, the Yellow Pages, and so on). Otherwise, you must specify the IP address of the MAX TNT.
If the accounting process of the daemon will be running on the same server as the authentication process (rather than on a separate host), the same password must also serve for the Acct-Key parameter in the Rad-Acct-Client subprofile of the External-Auth profile.
users in the /etc/raddb directory. A user is a caller that connects to the MAX TNT. The RADIUS users file contains security and configuration information for each user. The full set of information for each user is called a user profile.The MAX TNT can authenticate an incoming call locally or through RADIUS. Local authentication occurs when the caller's name and password match a Connection profile stored in the MAX TNT unit's memory. RADIUS authentication occurs when the caller's name and password match a user profile in the RADIUS
users file.For introductory information about the
users file and its format, see The users file. For details about creating user profiles to carry out various tasks, see the remaining chapters in this guide.
Creating the log file
Create a file called logfile in the /etc/raddb directory. RADIUS writes error messages to /etc/raddb/logfile. The Syslog daemon does not create the RADIUS log file, so you must create the file yourself. Specifying the MAX TNT unit's name and IP address
To enable the RADIUS host and the MAX TNT to communicate on the IP network, make sure that the MAX TNT unit's name and IP address are included in the /etc/hosts file on the RADIUS host or in the Yellow Pages database. Specifying the RADIUS daemon's authentication port
Use a text editor to open the /etc/services file and add a line identifying the port on which the RADIUS daemon receives authentication requests.
RADIUS 1812/udpThe port number you specify must match the port number indicated by the Auth-Port parameter in the Rad-Auth-Client subprofile of the External-Auth profile.
Configuring the MAX TNT to use the RADIUS server
This section describes how to configure the MAX TNT to communicate with the RADIUS daemon. You use the MAX TNT configuration interface to carry out each step. Some steps are required for all configurations. Others are optional, and depend on the needs of your site. For complete information about each parameter you set, see the MAX TNT Reference Guide.
Performing the required configuration steps
When configuring the MAX TNT to use RADIUS, you must specify:
To specify settings required for RADIUS operation:
The MAX TNT first tries to connect to the server specified by Auth-Server-1. If it receives no response within the time specified by the Auth-Timeout parameter, it tries to connect to Auth-Server-2. If it again receives no response within the time specified by Auth-Timeout, it tries to connect to Auth-Server-3. If the MAX TNT unit's request again times out, it reinitiates the process with Auth-Server-1. The MAX TNT can execute this cycle of requests a maximum of ten times.
the /etc/services file.
When you set Rad-ID-Space=Distinct, RADIUS authentication and accounting packets do not share the same ID sequence space. The MAX TNT can send a total of 256 authentication packets before the authentication ID sequence rolls over, and 256 accounting packets before the accounting ID sequence rolls over. Three sequence spaces are allocated: one for the Unified sequence space, one for the authentication ID sequence, and one for the accounting ID sequence.
When you configure the MAX TNT to use distinct ID sequence spaces, the RADIUS server must perform additional checks for duplicate detection. The server should check the RADIUS ID value as well as the service type and destination UDP port in each packet. The service type can be determined by sorting all values of the code field into two classes-Auth and Acct-and then comparing the received code value to determine to which class it belongs. The destination UDP port can be the same for both services when a single RADIUS server performs them.
If the MAX TNT does not receive a response within the time specified by Auth-Timeout, it sends the authentication request to the next server specified by the Auth-Server parameter.
Specifying the message resulting from a RADIUS timeout
By default, if authentication fails on a PPP connection because of a bad password or an authentication server timeout, the Ascend unit gracefully shuts down the PPP connection by sending an LCP-CLOSE request to the dial-up user. If Windows '95 (MSN) receives the LCP-CLOSE during authentication, it displays an invalid-password message. This message is misleading if the failure resulted from a RADIUS timeout. Example of configuring the MAX TNT to use the RADIUS server
The configuration illustrated in Figure 2-1 uses three RADIUS servers. Clients dialing in across the WAN use both framed and unframed protocols on analog and digital lines. The RADIUS daemon for each server receives client requests on UDP port 512, and the client password is tntpass.
Figure 2-1. Sample network topology for setting up the MAX TNT to use the RADIUS server
admin> read external-auth
EXTERNAL-AUTH read
admin> list
auth-type=none
acct-type=none
rad-id-space=unified
rad-id-source-unique=system-unique
rad-serv-enable=no
rad-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" no 0 no no no 0 yes +
rad-acct-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 0 acct-base-10 0 +
rad-auth-server={ 0 no rad-serv-attr-any [ 0.0.0.0 0.0.0.0 0.0.0.0 +
tac-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 }
tacplus-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 0 }
tacplus-acct-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" }
local-profiles-first=lpf-yes
admin> set auth-type=radius
admin> set rad-id-space=distinct
admin> list rad-auth-client
auth-server-1=0.0.0.0
auth-server-2=0.0.0.0
auth-server-3=0.0.0.0
auth-port=0
auth-src-port=0
auth-key=""
auth-pool=no
auth-timeout=0
auth-rsp-required=no
auth-id-fail-return-busy=no
auth-id-timeout-return-busy=no
auth-sess-interval=0
auth-TS-secure=yes
auth-Send67=yes
auth-frm-adr-start=no
auth-reset-time=0
admin> set auth-server-1=10.1.2.1
admin> set auth-server-2=10.1.2.2
admin> set auth-server-3=10.1.2.3
admin> set auth-port=512
admin> set auth-key=tntpass
admin> set auth-rsp-required=yes
admin> set local-profiles-first=lpf-no
admin> set auth-sess-interval=60
admin> set auth-src-port=500
admin> set auth-send67=no
admin> set auth-timeout=10
admin> write external-auth
EXTERNAL-AUTH written
Every time you reset the server with the Set command, the MAX TNT generates an SNMP trap. The MAX TNT also generates a trap if it changes to the next server because the current server fails to respond. The trap is an Enterprise Specific Trap (18), and is accompanied by the Object ID and IP address for the new server. The Object ID for Authentication Server is 1.3.6.1.4.1.529.13.3.1.11.x, where x is the index of the current server (1-3).
The following MIB objects support changing the current RADIUS authentication server:
radAuthHostIPAddress OBJECT-TYPE
SYNTAX IpAddress
ACESS read-only
STATUS mandatory
DESCRIPTION "The IP address of the Authentication server.
The value 0.0.0.0 is returned if entry is invalid."
::= { radiusAuthStatsEntry 11 }
radAuthCurrentServerFlag OBJECT-TYPE
SYNTAX INTEGER {
standby(1),
current(2)
}
ACCESS read-write
STATUS mandatory
DESCRIPTION "Value indicates whether this entry is the
current authentication server or not. Writing any value
will cause the current server to be reset to the primary
server (Host #1)."
::= { radiusAuthStatsEntry 12 }
Configuring the MAX TNT for RADIUS client requests
As an option, you can configure the MAX TNT to accept RADIUS requests from clients to disconnect a link or change filters for a particular session, user, or IP address. To do so, you need to write your own RADIUS client software that performs disconnects or changes filters. Then, you need to set up the MAX TNT and set several RADIUS attributes.
The process of configuring the MAX TNT for client requests involves both required and optional steps. You perform all the steps by setting parameters in the Rad-Auth-Server subprofile of the External-Auth profile.
Performing the required steps for client requests
You must specify the clients permitted to make requests, and the secret shared between each client and the RADIUS server. Specifying the clients permitted to make RADIUS requests
To specify the clients permitted to make RADIUS requests, you must use one of the following settings:
For example, you can specify values like the following:
If you set Auth-Session-Key=Yes, you must set the Auth-Attribute-Type parameter to specify the attributes required for identification of a user session. You can specify one of the following values:
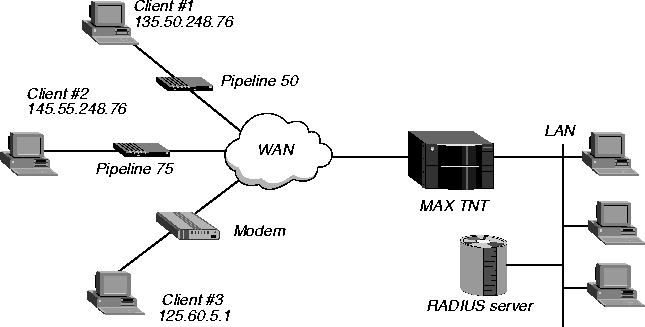
Figure 2-2. Sample network topology for setting up the MAX TNT to accept client requests
secret001 for client #1, secret002 for client #2, and secret003 for client #3. Each client must send the session key specified by the Ascend-Session-Svr-Key attribute. To set the values for the sample configuration, you would proceed as follows:
admin> read external-auth
EXTERNAL-AUTH read
admin> list
auth-type=none
acct-type=none
rad-id-space=unified
rad-id-source-unique=system-unique
rad-serv-enable=no
rad-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" no 0 no no no 0 yes +
rad-acct-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 0 acct-base-10 0 0+
rad-auth-server={ 0 no rad-serv-attr-any [ 0.0.0.0 0.0.0.0 0.0.0.0 +
tac-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 }
tacplus-auth-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" 0 0 }
tacplus-acct-client={ 0.0.0.0 0.0.0.0 0.0.0.0 0 0 "" }
local-profiles-first=lpf-yes
admin> list rad-auth-server
auth-port=1700
auth-session-key=no
auth-attribute-type=rad-serv-attr-any
auth-client=[ 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0+
auth-netmask=[ 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 +
auth-key=[ "" "" "" "" "" "" "" "" "" ]
admin> list auth-client
auth-client[1]=0.0.0.0
auth-client[2]=0.0.0.0
auth-client[3]=0.0.0.0
auth-client[4]=0.0.0.0
auth-client[5]=0.0.0.0
auth-client[6]=0.0.0.0
auth-client[7]=0.0.0.0
auth-client[8]=0.0.0.0
auth-client[9]=0.0.0.0
admin> set 1=135.50.248.76
admin> set 2=145.55.248.76
admin> set 3=125.60.5.1
admin> list ..
auth-port=1700
auth-session-key=no
auth-attribute-type=rad-serv-attr-any
auth-client=[ 135.50.248.76 145.55.248.76 125.60.5.1 0.0.0.0 0.0.0.0 +
auth-netmask=[ 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 +
auth-key=[ "" "" "" "" "" "" "" "" "" ]
admin> list auth-key
auth-key[1]=""
auth-key[2]=""
auth-key[3]=""
auth-key[4]=""
auth-key[5]=""
auth-key[6]=""
auth-key[7]=""
auth-key[8]=""
auth-key[9]=""
admin> set 1=secret001
admin> set 2=secret002
admin> set 3=secret003
admin> list ..
auth-port=1700
auth-session-key=no
auth-attribute-type=rad-serv-attr-any
auth-client=[ 135.50.248.76 145.55.248.76 125.60.5.1 0.0.0.0 0.0.0.0 +
auth-netmask=[ 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 +
auth-key=[ ********** ********* ********* "" "" "" "" "" "" ]
admin> set auth-session-key=yes
admin> set auth-attribute-type=rad-serv-attr-key
admin> write
EXTERNAL-AUTH written
Starting the RADIUS daemon
You can use one of two RADIUS daemons-radiusd or radiusd.dbm.
radiusd with a flat ASCII users file.
radiusd.dbm if you convert the flat ASCII users file to a standard UNIX DBM database.
The DBM database is no more difficult to use than the flat ASCII file, and is much faster. However, if you reset passwords, the new passwords take effect only after you rebuild the database. If resetting expired passwords is an important component of your system, the flat ASCII file might be the better choice.
users file, enter the following command:
radiusd [-A acct [-a acctdir]] [-c] [-d dbdir] [-p] [-s] [-u usrfile] [-v] [-w] [-x]Table 2-1 lists each argument.
Running the daemon with a UNIX DBM database
To run the daemon with a UNIX DBM database, you must carry out three tasks:
builddbm and radiusd.dbm.
builddbm file enables you to create the DBM database.
radiusd.dbm file is the version of the RADIUS daemon that you run when using the DBM database.
builddbm and radius.dbm executable files, enter the following command:
make dbm
radiusd.dbm, you must create the DBM database. To do so, enter the following command line:
builddbm [-d dbdir] [-e] [-h] [-u usrfile] [-v]
builddbm each time you modify the users file. If remote users are
able to change their own expired passwords, you must run builddbm after each password
change.
Table 2-2 list each argument for the builddbm command.
Starting the RADIUS daemon for a DBM database
To start the RADIUS daemon in DBM mode, enter the following command:
radiusd.dbm command supports the same set of arguments described for the radiusd command in Running the daemon with a flat ASCII users file, with one exception: The -p argument is restricted when the daemon is running in DBM mode. The users-file database will not contain the user's new password until you run builddbm again.
Copyright © 1998, Ascend Communications, Inc. All rights reserved.