
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


Getting Acquainted with RADIUS
This chapter introduces RADIUS authentication and accounting, and provides an overview of the files that the RADIUS server uses. The chapter consists of the following sections:
What is RADIUS?
RADIUS is an acronym for Remote Authentication Dial-In User Service. The MAX TNT uses RADIUS as a central location for storing:
- Authentication attributes
- Configuration data for establishing a WAN connection with an incoming call
- Routing information
- Dialout information
- Filters
- Accounting information
RADIUS maintains authentication, incoming call configuration, dialout, routing, and filter information in individual user profiles. Each user profile consists of a series of attributes. The attributes indicate a user name and password. They also enable you to configure routing, call management, and restrictions on the types of MAX TNT resources a caller can access.
How does RADIUS authentication work?
A RADIUS server is the machine on which the RADIUS daemon is running. A single RADIUS server can administer multiple security systems, maintaining profiles for thousands of users. RADIUS authentication is specified in IETF RFC 2058.
When you use RADIUS authentication, the following events take place:
- A user dialing in from a modem, ISDN terminal adapter, or router attempts to open a
connection to the MAX TNT.
- The MAX TNT determines that it must use a RADIUS user profile to authenticate the
user.
- The MAX TNT sends the user connection request to the RADIUS server.
- If you specify Calling-Line ID (CLID) authentication, the RADIUS server checks the
calling party's phone number. The RADIUS server can also perform called-number
authentication by checking the number the user dialed to reach the MAX TNT.
- If required, RADIUS obtains the user's name and password with Password Authentication
Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), or Microsoft
CHAP (MS-CHAP) authentication.
- If the user specified a UNIX user name and password, RADIUS performs a UNIX login.
- If you have configured token-card authentication, RADIUS forwards the connection
request to an external authentication server, such as a Security Dynamics ACE/Server or
Enigma Logic SafeWord server.
- The RADIUS server sends an authentication response to the MAX TNT. If authentication
is unsuccessful, the connection is refused. If authentication is successful, the MAX TNT
receives a list of attributes from the user profile in the RADIUS server's database and
establishes network access for the caller.
- The MAX TNT notifies the RADIUS server that the session has begun. The MAX TNT
also notifies the RADIUS server when the session ends. If you have accounting enabled,
the RADIUS server can generate accounting records.
How does RADIUS accounting work?
RADIUS accounting, specified in IETF RFC 2059, is a way to log information about three types of events:
- Start session. Denotes the beginning of a session with the MAX TNT. Information about this event appears in an accounting Start record.
- Stop session. Denotes the end of a session with the MAX TNT. Information about this event appears in an accounting Stop record.
- Failure-to-start session. Denotes that a login attempt has failed. Information about this event appears in an accounting Failure-to-start record.
When the MAX TNT recognizes one of these events, it sends an accounting request to RADIUS. When the accounting server receives the request, it combines the information into a record and timestamps it. Each type of accounting record contains attributes associated with an event type, and can show the number of packets the MAX TNT transmitted and received, the protocol in use, the user name and IP address of the client, and so on.
You can use RADIUS accounting to:
- Gather billing information, including who called, how long the session lasted, and how much traffic occurred during the session.
- Troubleshoot RADIUS and MAX TNT operations. Accounting records can contain information about how many login failures occurred, and can describe the characteristics of the failed attempts.
What types of applications does RADIUS support?
This section describes some common RADIUS applications.
Simple RADIUS authentication and accounting
In Figure 1-1, the RADIUS server performs both authentication and accounting.
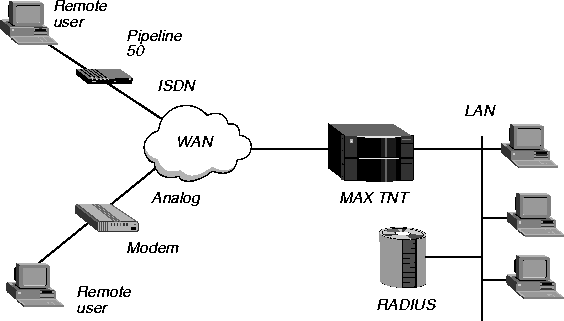
Figure 1-1. RADIUS authentication and accounting
This configuration is ideal for cost-conscious service providers and corporations that do not want to invest in different machines for security and backup.
RADIUS authentication and accounting with a backup server
In Figure 1-2, a service provider or corporate office has a second RADIUS server acting as a backup. If the primary RADIUS server fails, the MAX TNT automatically contacts the secondary RADIUS server to authenticate a user. If the secondary server fails, you can bring in a third RADIUS server as a backup. You can use the secondary server as a backup accounting server as well.
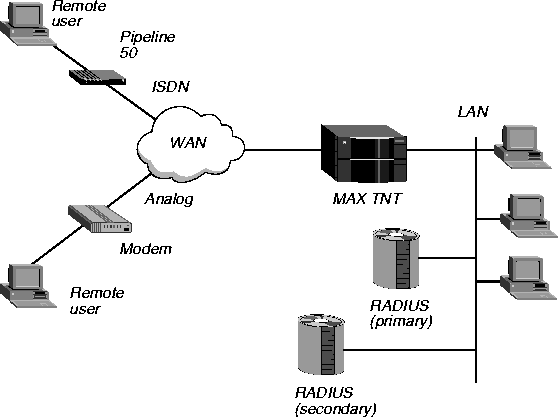
Figure 1-2. RADIUS authentication and accounting with a backup server
RADIUS with an external token-card server
For more secure networks, a service provider or corporate office can use RADIUS as a front end to a token-card authentication server, such as Security Dynamics ACE/Server or Enigma Logic's SafeWord server. Figure 1-3 illustrates an environment that includes an Ascend Pipeline as the calling unit, a MAX TNT functioning as a Network Access Server (NAS), a RADIUS server, and an external token-card server.
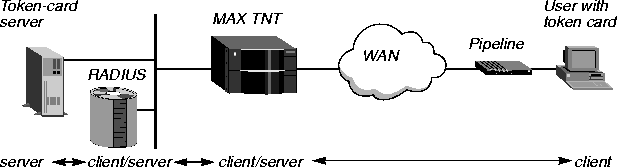
Figure 1-3. RADIUS with an external token-card server
For complete information about configuring RADIUS to work with token-card authentication servers, see Setting up token-card authentication.
Using RADIUS to sign up new customers
In Figure 1-4, the service provider has a RADIUS server and a separate registration server. When a new customer connects to the network with a specific name and password found in the company's advertising, the MAX TNT passes the request to the registration server. The server prompts the user to enter sign-up information.
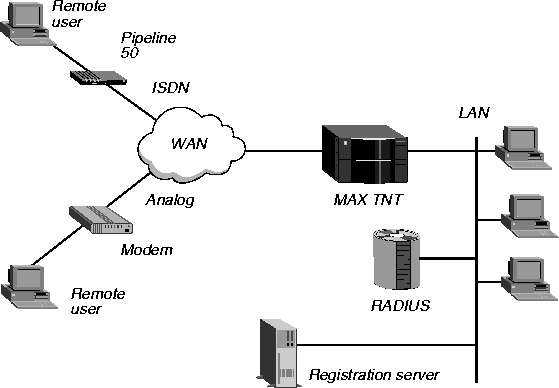
Figure 1-4. Using RADIUS to sign up new customers
A user cannot access any other resource on the system before providing all the registration details and signing up for the service. After a user completes the registration procedure, the server issues a permanent user name and password.
What files does RADIUS use?
The RADIUS server uses the files listed in Table 1-1.
Table 1-1. RADIUS files
File name
|
Default location
|
Description
|
|---|
radiusd
|
/etc/raddb
|
RADIUS daemon for a flat ASCII users file.
You must use the Ascend RADIUS daemon, version 1.16 (dated 7/25/95) or later if you require RADIUS accounting or any of the Ascend extensions to the RADIUS daemon defined by IETF RFC 2058.
For information about running the radiusd daemon, see Running the daemon with a flat ASCII users file.
|
radiusd.dbm
|
/etc/raddb
|
RADIUS daemon for a UNIX DBM database.
You must use the Ascend RADIUS daemon, version 1.16 (dated 7/25/95) or later if you require RADIUS accounting or any of the Ascend extensions to the RADIUS daemon defined by IETF RFC 2058.
For information about running the radiusd.dbm daemon, see Running the daemon with a UNIX DBM database.
|
dictionary
|
/etc/raddb
|
Ascend RADIUS dictionary. This file contains a list of all the attributes the daemon supports, along with the possible values for each attribute.
You must install the dictionary on your RADIUS server in the same directory as the Ascend RADIUS daemon, and it must have the same date as the Ascend RADIUS daemon. The RADIUS daemon reads the dictionary when it starts up. If you update the dictionary file while the daemon is running, you must stop the daemon process and restart it to make the new attributes available.
For further information about the dictionary file, see The dictionary file.
|
clients
|
/etc/raddb
|
File that identifies each client that can send requests to the RADIUS server. For overview information about the clients file, see The clients file. For details about setting up the clients file, see Creating and configuring the clients file.
|
users
|
/etc/raddb
|
File that contains a set of user profiles. Each user profile consists of attributes describing the user's name, his or her password, and the MAX TNT features to which the user has access.
For introductory information about the users file, see The users file. For details about setting up the users file, see Chapter 3, Setting Up RADIUS Authentication and all succeeding chapters in this guide.
|
logfile
|
/etc/raddb
|
File containing error messages. You must create this file yourself.
|
detail
|
/usr/adm/NAS-name/radacct
|
File containing accounting records.
|
The dictionary file
Every attribute has a name, ID, and value type. The dictionary file provides a complete list of attributes, and contains the information described in Table 1-2.
The first several lines of a typical dictionary file might look like the following:
ATTRIBUTE User-Name 1 string
ATTRIBUTE Password 2 string
ATTRIBUTE Challenge-Response 3 string
ATTRIBUTE NAS-Identifier 4 string
ATTRIBUTE NAS-Port 5 string
The clients file
A client is the MAX TNT or another machine that sends requests to the RADIUS server. The RADIUS clients file defines the client machines permitted to make requests to the RADIUS server. For the RADIUS daemon to respond to client requests from the MAX TNT, you must enter a line specifying the MAX TNT unit's name and password in the clients file. For example:
Ascend3 bXSAMpy
The users file
The users file is a text file that can contain both user profiles and pseudo-user profiles.
- A user profile is an entry for a user that RADIUS will authenticate. It consists of attributes describing a user and the services he or she can access.
- A pseudo-user profile is an entry containing information that the MAX TNT can query. It does not exist for the purpose of authenticating a user. Rather, it enables you to specify static route configurations, Frame Relay profile information, and other types of data.
Note: Every attribute name and value is case sensitive. For more complete information about
setting up the users file, see Using the RADIUS interface.
Overview of RADIUS packet formats
Each RADIUS packet consists of the fields listed in Table 1-3.
Table 1-3. RADIUS packet fields
Element
|
Description
|
|---|
|
Code (8 bits)
|
Specifies the packet type. For a list of packet types, see Table 1-4.
|
|
Identifier (8 bits)
|
Enables RADIUS to match requests with responses. Each new request has a unique identifier. Each response carries the identifier of the corresponding request.
|
|
Length (16 bits)
|
Indicates the total packet size in bytes.
|
|
Authenticator (16 bytes)
|
Authenticates packets between the NAS and the authentication server. The NAS and the authentication server share a secret that the system uses, along with the authenticator field, to provide password encryption and packet authentication. The shared secret resides in the clients file on the authentication host.
The MAX TNT checks all authentication and accounting packets to ensure that they come from known sources. The check makes use of the shared secret, the authenticator field, and MD5 encoding. In addition, all passwords that the MAX TNT sends are encrypted with MD5, CHAP, or DES. Passwords that the authentication server sends can be encrypted with MD5.
|
|
Attribute list (variable length)
|
Consists of zero or more attributes. Each attribute consists of the following fields:
Attribute ID (8 bits)-These IDs are in the dictionary file.
Attribute length (8 bits)-This field shows the combined length of the ID, length, and value fields.
Attribute value (variable length)-The length and format of this value depend on the attribute type.
|
Table 1-4 lists the packet types that can appear in the code field.
Using the RADIUS interface
To set up RADIUS, you must configure attributes in the users file. Table 1-5 lists each element of the users file.
Table 1-5. Elements of the users file
Element
|
Description
|
|---|
|
Comment line
|
Begins with the # character at column one, followed by text that extends to the end of the line.
|
|
Pseudo-user profile
|
Consists of the same elements as the user profile, except that the attributes specify information that the MAX TNT can query, rather than authentication information.
|
|
User profile
|
Consists of a first line (also called an authentication line), followed by the rest of the profile, including a final line.
The first line consists of a user name, followed by a space or tab, followed by an attribute list containing authentication information, such as the user's password and the password's expiration date. The attributes on the first line are called check attributes, because RADIUS must check the attributes before it can grant access to the MAX TNT.
Columns one and two may contain any characters except the # character, a space, or a tab. Starting at the third column, the first line may contain one or more spaces or tabs, followed by an attribute list (without a trailing comma) and a newline.
Each subsequent line in the rest of the record has a space or tab in the first column, followed by zero or more spaces or tabs, an attribute list, a comma, and a newline.
The final line is identical to each line after the first one, except that it contains no trailing comma.
|
|
Blank line
|
A blank line must not appear within a profile, but may be present anywhere outside a profile. It must end with a newline.
|
When setting an attribute in a profile, you specify the name of the attribute, followed by an equal sign (=), followed by the attribute's setting. For attributes with predefined settings, you can spell out the full setting, or specify a numeric equivalent. For instance, you can set the User-Service attribute to Login-User (1) in either of the following ways:
User-Service=Login-User
User-Service=1
The following example of part of a users file includes two comment lines, a blank line, and a user profile:
# This user profile is for PPP sessions only, and uses a
# local password.
Ascend1 Password="Pipeline"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=10.0.1.1,
Framed-Netmask=255.255.255.0,
Ascend-Metric=2,
Framed-Routing=None,
Ascend-Idle-Limit=30
The user profile consists of a first line containing the user name (Ascend1) and password (Pipeline) that the RADIUS server uses for authentication. Subsequent lines contain attributes describing the type of service the user can access, the type of protocol in use, and so on. Each line of the profile, except the first line and last line, contains a trailing comma.
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.

