
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


Setting Up RADIUS Authentication
This chapter discusses how to configure the RADIUS server to authenticate MAX TNT clients. It consists of the following sections:
Before you begin
Before you begin configuring RADIUS authentication, you must set up the MAX TNT to require a profile for authentication. In addition, depending on the needs of your site, you can optionally configure the MAX TNT to:
- Check for a RADIUS profile before a local Connection profile.
- Use E1 Chinese signaling and Calling-Line ID (CLID) authentication.
- Return the User Busy (17) Cause Element in ISDN Disconnect packets.
Requiring the MAX TNT to use a profile for authentication
To require a profile for authentication, set Profiles-Required=Yes in the Answer-Defaults profile at the MAX TNT configuration interface.
Configuring the MAX TNT to check for a RADIUS profile first
If you want the MAX TNT to check for a RADIUS profile before looking for a local Connection Profile, set Local-Profiles-First=LPF-No in the External-Auth profile at the MAX TNT configuration interface. If the remote server acknowledges the request, the MAX TNT allows the connection. If the server does not respond, or if the server sends a NAK (because it could not find a profile, or the profile it found did not contain a matching password), the MAX TNT checks for a matching local profile.
If you set Local-Profiles-First=LFP-RNo and the remote server returns a NAK, the MAX TNT terminates the connection.
Configuring the MAX TNT for E1 Chinese signaling
If Signaling-Mode=E1-Chinese-Signaling, and you plan to set up Calling-Line ID (CLID) or called-number authentication in RADIUS, you must set Caller-ID=Get-Caller-ID in the Line-Interface subprofile of the E1 profile.
Specifying User Busy (17) in ISDN Disconnect packets
When CLID or called-number authentication fails, the MAX TNT can return either User Busy (decimal 17) or Normal Call Clearing (decimal 16) as the Cause Element in ISDN Disconnect packets.
The default behavior is to send Normal Call Clearing (16). You can specify that the MAX TNT return User Busy (17) by setting the following values in the Rad-Auth-Client subprofile of the External-Auth profile:
- Auth-ID-Fail-Return-Busy=Yes. This setting specifies that the MAX TNT sends User Busy (17) when CLID or called-number authentication fails.
- Auth-ID-Timeout-Return-Busy=Yes. This setting specifies that the MAX TNT sends User Busy (17) when CLID or called-number authentication times out.
Overview of RADIUS authentication
This section describes how the MAX TNT uses RADIUS authentication when answering a call. By default, when you require a profile for authentication, the MAX TNT always checks for a Connection profile. If a Connection profile does not exist, or if a Connection profile exists but the password fails, the MAX TNT checks for a remote RADIUS, TACACS, or TACACS+ profile. However, you can change this default by setting Local-Profiles-First=LPF-No or Local-Profiles-First=LPF-RNo in the External-Auth profile.
This section assumes that the MAX TNT looks for a local profile first. For an incoming call, the MAX TNT carries out the following authentication steps:
- Before the MAX TNT answers a call, it determines whether or not the Answer-Defaults
profile requires Calling-Line ID (CLID) authentication, called-number authentication, or
both.
The CLID is the phone number of the calling device, which is not always provided by the WAN carrier. When the profile requires CLID authentication, the telco-provided caller ID must match a phone number specified in a local Connection profile or RADIUS user profile.
The called-party number is the phone number the remote device called to connect to the MAX TNT, but without a trunk group or dialing prefix specification. This number is always available if specified in a profile. When the profile requires called-number authentication, the number called must match a called-party number in a local Connection profile or RADIUS user profile.
- If the profile requires CLID authentication (CLID-Auth-Mode=CLID-Require in the
Answer-Defaults profile) or called-number authentication (CLID-Auth-Mode is set to
DNIS-Require in the Answer-Defaults profile), the MAX TNT first looks for a matching
phone number in a local Connection profile.
If one does not exist, it then looks for a matching phone number in a RADIUS user profile. If it cannot find the correct phone number, the MAX TNT hangs up.
- If the profile does not require CLID or called-number authentication, or if the MAX TNT
finds a matching phone number in a local Connection profile or RADIUS user profile, it
answers the call.
- The MAX TNT routes the call.
- The MAX TNT checks its other Answer-Defaults profile settings.
- If the Answer-Defaults profile specifies the type of link encapsulation the call uses, the
MAX TNT continues checking Answer-Defaults parameters.
If the Answer-Defaults profile does not enable the type of link encapsulation the call uses, the MAX TNT drops the call.
- The MAX TNT checks the value of the Profiles-Required parameter in the
Answer-Defaults profile.
If Profiles-Required=Yes, the MAX TNT must find a Connection profile, RADIUS user profile, TACACS profile, or TACACS+ profile to authenticate the call.
- If a profile is required, the MAX TNT checks to see whether the profile must contain a
matching user name and password.
If Receive-Auth-Mode=PAP-PPP-Auth, CHAP-PPP-Auth, MS-CHAP-PPP-Auth, or Any-PPP-Auth, the MAX TNT requires a matching name and password as a condition of authentication.
- For IP routing connections, the MAX TNT looks for a Connection profile that matches the
client's IP address.
If it cannot find a Connection Profile, it looks for a RADIUS, TACACS, or TACACS+ profile. The MAX TNT then uses the name and password in the profile to authenticate the session. If the MAX TNT does not find a matching IP address (perhaps because the MAX TNT assigns addresses dynamically), it searches for a profile that matches the name and password that the dial-in client presents.
- If name and password authentication is required, the MAX TNT attempts to match the
caller's name and password to a local Connection profile.
If authentication succeeds using a local Connection profile, the MAX TNT uses the parameters specified in the profile to build the connection.
- If it cannot find a matching Connection profile, the MAX TNT looks for a RADIUS,
TACACS, or TACACS+ profile containing a matching name and password.
If authentication succeeds using a RADIUS user profile, the MAX TNT uses the specified RADIUS attributes to build the connection. The MAX TNT can then forward the call to its router or other destination. For example, the MAX TNT might forward a terminal-server call to a Telnet or TCP host.
If authentication succeeds using a TACACS or TACACS+ profile, the MAX TNT must make a request to the server for information about the resources and services the user can access.
- If name and password authentication is not required (Receive-Auth-Mode=No-PPP-Auth),
the MAX TNT can use the IP address specified by the Connection profile to match
IP-routed PPP calls.
- If the Answer-Defaults profile does not require a profile (Profiles-Required=No), the
MAX TNT uses the Answer-Defaults parameters to build the connection.
- After building the session, the MAX TNT passes the data stream to the appropriate
software module or host.
Overview of RADIUS authentication tasks
All RADIUS authentication tasks are optional, and depend upon your security needs. Most configurations use name and password authentication, as described in Setting up name and password authentication. If you require callers to supply a name and password, you must specify the authentication protocol to use for incoming calls. For instructions, see Specifying an access protocol for incoming calls.
Other tasks include:
Setting up name and password authentication
Name and password authentication is the simplest form of authentication for incoming calls from remote users across the WAN. Such connections use a setup similar to the one illustrated in Figure 3-1.
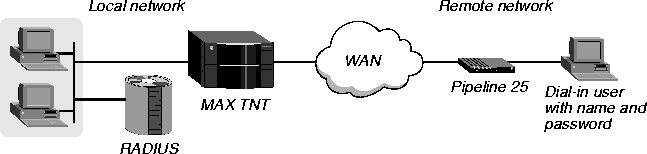
Figure 3-1. Setting up name and password authentication for incoming calls
If you plan to use PAP, CHAP, or MS-CHAP authentication, you must specify a name and password in a RADIUS user profile. Carry out the following tasks:
- Specify the name of the remote user or device with the User-Name (1) attribute.
- Specify the password with the Password (2) attribute.
Depending on your needs, you also have the option of configuring password expiration and pseudo-user profiles.
Specifying a user name
The user name must be the first value on the first line of a RADIUS profile. Specify an alphanumeric string of up to 252 characters. You need not specify the User-Name= portion of the setting. Rather, you can simply specify the user name itself. The default value is null. Because the MAX TNT uses the first matching name for an incoming caller, you must not specify a duplicate user name in any RADIUS user profile.
Using the caller's name
In most instances, the User-Name attribute specifies the name of the calling device or dial-in user. For example, in the following first line of a user profile, Emma is the name of a dial-in user:
Emma Password="pwd", Ascend-PW-Expiration="Jan 30 1997"
The RADIUS server tests the user's name and password against the values the user provides when making a request for access. If the RADIUS server does not find a match, it denies the request for access.
Using the Default keyword
You can also specify the user name Default. The RADIUS server uses the Default profile to determine the kind of access it grants to users who do not appear in the users file. You can configure only one Default profile. It must specify the user name Default, and it must be the last profile in the users file.
For example, the following first line of a profile enables a terminal-server user to log in with his or her UNIX account name or password:
Default Password="UNIX"
Make sure that the Default profile is the last one in the file. RADIUS ignores any profiles that follow the Default profile.
Specifying a password
A user profile must contain an encrypted password to authenticate the caller. Specify a password by means of the Password attribute. The password must appear on the first line of the user profile, directly after the user name, and must be an alphanumeric string of up to 252 characters. The default value is null.
Table 3-1 lists the specifications you can make for the Password attribute.
Configuring password expiration
The Ascend RADIUS daemon supports password aging and expiration, and includes a method for enabling dial-in users to replace expired passwords. This section contains the following information about password expiration:
- Conditions for replacing expired passwords
- Setting the password expiration attributes
- Changing a nonexpired password
- Changing an expired password
Conditions for replacing expired passwords
When the server is running the Ascend RADIUS daemon, and you have configured the daemon for expired passwords, a dial-in user can replace an expired password that meets all the following conditions:
Setting the password expiration attributes
The Ascend RADIUS daemon uses the attributes listed in Table 3-2 to support password aging and expiration.
To set up password expiration, you specify the Ascend-PW-Expiration attribute on the first line of the user profile. Then, you specify the Ascend-PW-Lifetime attribute on any line other than the first one.
Ascend-PW-Expiration
Ascend-PW-Expiration specifies an expiration date for a user's password. When the MAX TNT makes an authentication request, the RADIUS server checks the current date against the value of Ascend-PW-Expiration. If the date of the authentication request is the same or a later date than the value of Ascend-PW-Expiration, the user receives a message saying that the password has expired.
You must specify Ascend-PW-Expiration when you first create a user, and it must appear on the first line of the user profile. If it appears after the first line, RADIUS does not check the expiration date and could accept an expired password. Your specification might look like this one:
Emma Password="pwd", Ascend-PW-Expiration="Jan 1, 1997"
Ascend-PW-Lifetime
Ascend-PW-Lifetime specifies the number of days that a password is valid. Your specification might look like this one:
Emma Password="pwd", Ascend-PW-Expiration="Jan 1, 1997"
Ascend-PW-Lifetime=30,
...
Ascend-PW-Lifetime applies only to the process of renewing an expired password. When the user wants to renew the password, the MAX TNT adds the value you specify for Ascend-PW-Lifetime to the current date and updates the user profile.
How Ascend-PW-Expiration and Ascend-PW-Lifetime work together
If a password expires and the user resets it, the RADIUS server adds the value of Ascend-PW-Lifetime to the date on which the user resets the password. The resulting date becomes the new value for Ascend-PW-Expiration.
For example, suppose that today's date is March 1, 1997 and the following lines appear in a user profile:
Emma Password="pwd", Ascend-PW-Expiration="Jan 1, 1997"
Ascend-PW-Lifetime=30,
...
If the user resets the password today, the value of Ascend-PW-Expiration becomes today's date plus Ascend-PW-Lifetime, or March 31, 1997.
If the password has not expired, the value of Ascend-PW-Lifetime is irrelevant. For example, suppose that today's date is January 1, 1997 and the following lines appear in a user profile:
Emma Password="pwd", Ascend-PW-Expiration="Jan 15, 1997"
Ascend-PW-Lifetime=30
...
The password expires on January 15, 1997.
If Ascend-PW-Lifetime is absent, the value of Lifetime-In-Days determines the password duration. The Lifetime-In-Days value in the RADIUS dictionary is the default value for Ascend-PW-Lifetime. By default, Lifetime-In-Days is 0 (zero). This value means that passwords do not expire.
Note: If you run the Ascend RADIUS daemon with a flat ASCII file, RADIUS accepts a
user's replacement for an expired password only if you start the daemon with the -p argument.
For details, see Running the daemon with a flat ASCII users file. If you run the daemon in
DBM mode, RADIUS accepts a user's replacement for an expired password if you specify the
-p argument, but does not recognize the new password until you rebuild the users-file
database by running builddbm again. For information, see Creating the DBM database.
Changing a nonexpired password
The MAX TNT supports a Password command that enables a RADIUS-authenticated terminal-server user to change his or her password. To change a password:
- Enable password expiration in the user profile, following the instructions in Configuring
password expiration.
When you change a nonexpired password, the MAX TNT uses the same mechanism that enables you to enter a new password when an older one has expired.
- At the terminal-server prompt, enter the Password command:
ascend% Password
The following prompts appear:
Enter old password:
Enter new password:
Re-type new password:
- At the
Enter old password prompt, specify the current password.
- At the
Enter new password and Re-type new password prompts, enter the
new password. The new password cannot be null, and must differ from the old password.
If the password change is successful, the following message appears:
Password Updated
If the update fails for any reason, the following message appears:
Password NOT Changed
There is no indication of why the password change failed. You might have entered the old password incorrectly. Or you might be trying to change a UNIX password. You cannot change a UNIX password with the Password command, because a UNIX password is not stored in the RADIUS database.
Changing an expired password
When a user attempts to establish a terminal-server connection with an expired password, the following events take place:
- The MAX TNT informs the user that the authentication failed because the password has
expired.
- The MAX TNT prompts the user for a new password.
If the new password is null or matches the old password, the MAX TNT prompts the user again for a new password.
If the new password is valid, the MAX TNT asks the user to re-enter it for confirmation. If the two entries do not match, the MAX TNT prompts again for a new password.
- After receiving a valid confirmation of the new password, the MAX TNT contacts the
RADIUS server for acceptance of the new password.
If the RADIUS server accepts the new password, it reports the successful change.
If the RADIUS server rejects the new password, it informs the user and prompts again for a new password. The RADIUS server can reject the password change for any of the following reasons:
Configuring the name and password in pseudo-user profiles
A pseudo-user profile contains information that the MAX TNT can query. It does not exist for the purpose of authenticating a user. Rather, it enables you to specify static route configurations, Frame Relay profile information, and other types of data.
Along with other attributes on the first line, the values you specify for User-Name and Password determine how the MAX TNT uses the profile. Table 3-3 describes how to set up the first line of a pseudo-user profile for various purposes. Each entry of the table contains a reference for information about completing the rest of the profile.
Some profiles use the following arguments:
- name is the system name of the Ascend unit (the name specified by the Name parameter in the System profile).
- num is a number in a sequential series, starting at 1.
Note: The first line of a pseudo-user profile cannot use newlines. The specifications appear
on multiple lines here for printing purposes only.
Table 3-3. First-line configuration of pseudo-user profiles
Element configured
|
First-line specification
|
|---|
|
Outgoing calls
|
For the User-Name attribute, specify the name of the remote device that will receive outgoing calls, appending -Out to the user name. Then, set Password="ascend" and User-Service=
Dialout-Framed-User. The User-Service setting ensures that no one can use the profile for authentication of an incoming call.
For complete information, see Setting up an outgoing PPP, MP, or MP+ connection.
|
|
Nailed/MPP connection
| permconn-name-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up a Nailed/MPP connection.
|
|
Nailed-up connection
| permconn-name-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up a nailed-up connection.
|
|
Message text and list of hosts
|
For a configuration specific to a single MAX TNT unit:
initial-banner-name Password="ascend",
User-Service=Dialout-Framed-User
For a configuration used by several MAX TNT units:
initial-banner Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up the message text and a list of hosts.
|
|
Frame Relay profile
| frdlink-name-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up the logical link to a Frame Relay switch.
|
|
Frame Relay user profile
| permconn-name-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up Frame Relay user connections.
|
|
IP address pools
| pools-name Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Defining a pool of addresses for dynamic assignment.
|
|
Static IP routes
|
For an IP dialout route specific to a single MAX TNT unit:
route-name-num Password="ascend", User-Service=
Dialout-Framed-User
For an IP dialout route used by several MAX TNT units:
route-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up static IP routes.
|
|
Static IPX routes
|
For an IPX dialout route specific to a single MAX TNT unit:
ipxroute-name-num Password="ascend", User-Service=
Dialout-Framed-User
For an IPX dialout route used by several MAX TNT units:
ipxroute-num Password="ascend", User-Service=
Dialout-Framed-User
For complete information, see Setting up static IPX routes.
|
Examples of setting up name and password authentication
This section contains sample profiles that show you how to set up name and password authentication for the following purposes:
- Authentication of a PPP connection, with or without password expiration
- Authentication using a Default profile for dial-in ISDN and modem users
Example of setting up name and password authentication for a PPP link
This example shows how to set up a simple user profile for a client dialing in over a PPP connection. Figure 3-2 illustrates the WAN configuration.
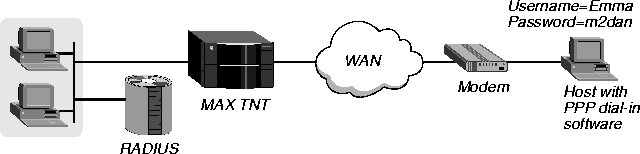
Figure 3-2. Setting up authentication of a PPP connection
The user's name is Emma and her password is m2dan. To allow a PPP connection that uses IP routing for an incoming call, you would configure Emma's user profile as follows:
Emma Password="m2dan", User-Service=Framed-User
Framed-Protocol=PPP,
Framed-Address=200.250.55.9,
Framed-Netmask=255.255.255.248,
Ascend-Route-IP=Route-IP-Yes
Example of setting up password expiration for a PPP connection
This example shows how to configure password expiration for the configuration described in Example of setting up name and password authentication for a PPP link. To specify that any password reset after January 1, 1997 lasts for 30 days, you would configure the user profile as follows:
Emma Password="pwd", Ascend-PW-Expiration="Jan 1, 1997"
Ascend-PW-Lifetime=30,
Framed-Protocol=PPP,
Framed-Address=200.250.55.9,
Framed-Netmask=255.255.255.248,
Ascend-Route-IP=Route-IP-Yes
Suppose that today's date is March 1, 1997. If the user resets the password today, the value of Ascend-PW-Expiration becomes today's date plus Ascend-PW-Lifetime, or March 31, 1997.
Example of setting up a Default profile for ISDN and modem clients
This example shows how to set up RADIUS to authenticate both ISDN users and modem dial-in connections that use PPP. The calling units reside at the remote end. The local end consists of a MAX TNT and a UNIX device running RADIUS, ACE/Client, and ACE/Server. The WAN configuration is illustrated in Figure 3-3.
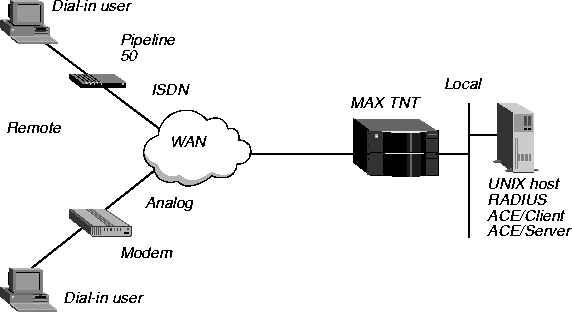
Figure 3-3. Setting up a Default user profile
In this example, all users must authenticate by means of Security Dynamics ACE/Server. The ISDN callers use PAP-Token-CHAP authentication. Modem users must enter their PIN and token passcodes. To set up the configuration, you would enter the following settings in the profile:
DEFAULT Password="ACE"
Ascend-Receive-Secret="test",
User-Service=Framed-User,
Framed-Protocol=MPP,
Ascend-Idle-Limit=120
Specifying the MAX TNT unit's name and password
When the MAX TNT places an outgoing call, it identifies itself by a login name and password. You have the option of overriding the system's default values by specifying a name and password in a RADIUS pseudo-user profile. Table 3-4 lists the MAX TNT unit's login name and password attributes, as well as the other attributes necessary, as a minimum, for an outgoing call.
To configure the MAX TNT unit's name and password for outgoing calls:
- On the first line of the profile, set the User-Name attribute to the name of the device that
will receive outgoing calls, and append -Out to the user name.
- Set the Password attribute to "ascend".
- Set User-Service=Dialout-Framed-User.
- On the second line, set the User-Name attribute to the name of the device that will receive
outgoing calls.
- On any succeeding line, set the Ascend-Authen-Alias attribute to the MAX TNT unit's
login name.
- Set the Ascend-Send-Passwd or Ascend-Send-Secret attribute to the MAX TNT unit's
password. (Use Ascend-Send-Passwd only if your version of the MAX TNT does not
support Ascend-Send-Secret.)
If the value you specify for Ascend-Send-Secret or Ascend-Send-Password does not match the value of the remote end's Ascend-Receive-Secret attribute (in a RADIUS user profile) or Recv-Password parameter (in a Connection profile), the remote system rejects the call.
Example of configuring the MAX TNT unit's login name and password
In Figure 3-4, the MAX TNT makes an outgoing call to another unit across the WAN.
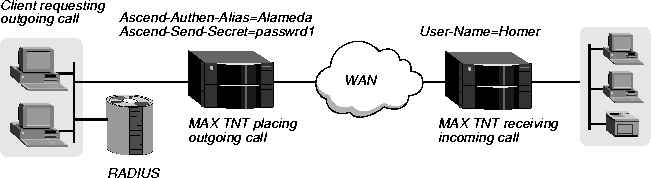
Figure 3-4. Configuring the MAX TNT unit's login name and password
The profile must include values for the Ascend-Authen-Alias and Ascend-Send-Secret attributes. In this example, you might configure the profile as follows:
Homer-Out Password="ascend", User-Service=Dialout-Framed-User
User-Name="Homer",
Ascend-Authen-Alias="Alameda",
Ascend-Send-Auth=Send-Auth-PAP,
Ascend-Send-Secret="passwrd1",
Ascend-Dial-Number="31",
Framed-Protocol=PPP,
Framed-Address=10.0.100.1,
Framed-Netmask=255.255.255.0,
Ascend-Metric=2,
Framed-Routing=None,
Framed-Route="10.5.0.0/24 10.0.100.1 1",
Ascend-Idle-Limit=30
Specifying whether multiple callers can use a profile
By default, the MAX TNT requires that a RADIUS user profile apply only to a single caller. However, you can configure the MAX TNT to allow multiple callers to use the same RADIUS user profile. More than one user can specify the same name and password. However, no two users can have the same IP address, and the IP address cannot be hard-coded into a RADIUS user profile. You must set up dynamic address assignment on the MAX TNT or in RADIUS.
You can set up shared profiles on a system-wide or per-profile basis.
- To specify that all RADIUS user profiles can apply to more than a single dial-in user, set Shared-Prof=Yes in the IP-Global profile at the MAX TNT configuration interface.
- To specify that a particular RADIUS user profile can apply to more than a single dial-in user, set Shared-Prof to No in the IP-Global profile and Ascend-Shared-Profile-Enable to Shared-Profile-Yes in the RADIUS user profile.
Example of setting up a RADIUS user profile for multiple callers
In Figure 3-5, multiple remote callers can enter the username David and the password mypassword to gain access to the MAX TNT.
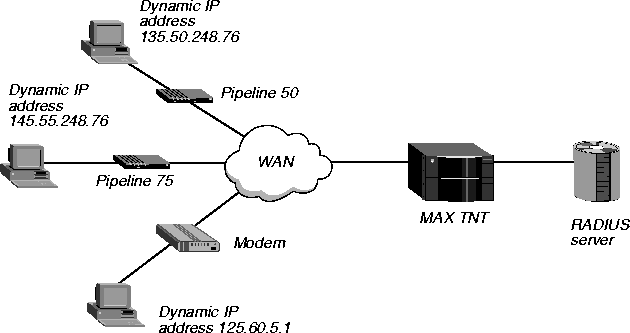
Figure 3-5. Setting up a shared profile
IP routing and PPP encapsulation are enabled, and each user is assigned an IP address from pool #1. With Shared-Prof=No in the IP-Global profile, you would configure the user profile as follows:
David Password="mypassword", User-Service=Framed-User
Framed-Protocol=PPP,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Assign-IP-Pool=1,
Ascend-Shared-Profile-Enable=Shared-Profile-Yes
Specifying an access protocol for incoming calls
The answering unit always determines the authentication method to use for the call. By default, the MAX TNT allows incoming calls without authentication. To indicate an authentication protocol for name and password authentication of PPP, MP, and MP+ calls, you must set the Receive-Auth-Mode parameter in the PPP-Answer subprofile of the Answer-Defaults profile. Specify one of the values listed in Table 3-5.
Table 3-5. Settings for the Receive-Auth-Mode parameter
Setting
|
Specifies
|
|---|
|
PAP-PPP-Auth
|
PAP, a PPP authentication protocol that provides a simple method for the MAX TNT to establish its identity in a two-way handshake. Authentication takes place only upon initial link establishment, and does not use encryption. The remote device must support PAP.
|
|
CHAP-PPP-Auth
|
CHAP, a PPP authentication protocol that is more secure than PAP. CHAP provides a way for the remote device to periodically verify the identity of the MAX TNT by means of a three-way handshake and encryption. Authentication takes place upon initial link establishment. A device can repeat the authentication process at any time after the connection is up. The remote device must support CHAP.
|
|
MS-CHAP-PPP-Auth
|
MS-CHAP, the Windows NT version of CHAP. This protocol uses DES and MD4 encryption. Using MS-CHAP, an Ascend unit can authenticate a Windows NT system, and a Windows NT system can authenticate an Ascend unit.
|
|
Any-PPP-Auth
|
PAP, CHAP, or MS-CHAP. The MAX TNT first tries to use MS-CHAP. If the remote end of the connection does not support it, the MAX TNT then attempts to use CHAP. If the remote end of the connection does not support CHAP, the MAX TNT uses PAP instead.
|
Consider the following:
- If the incoming PPP call does not include a source IP address, the MAX TNT requires PAP, CHAP, or MS-CHAP authentication.
- For modem or V.120 calls, PAP, CHAP, and MS-CHAP authentication are not available.
- You cannot specify a UNIX password if you are using CHAP authentication.
- For PAP, CHAP, and MS-CHAP authentication, the calling unit and the MAX TNT share a different secret with the RADIUS server.
- The calling unit's secret is called the remote secret. The MAX TNT does not know the remote secret's value.
- The MAX TNT unit's secret is called the NAS secret (because the MAX TNT is an NAS). The calling unit does not know the NAS secret's value.
How PAP works
For PAP authentication, the following events take place:
- The calling unit sends the unencrypted remote secret to the MAX TNT.
- The MAX TNT uses the NAS secret to encrypt the remote secret.
- The RADIUS server uses the NAS secret to decrypt the remote secret.
- The RADIUS server validates the remote secret, or passes the clear copy of the remote
secret to a UNIX or other password validation system.
Figure 3-6 illustrates how PAP works.
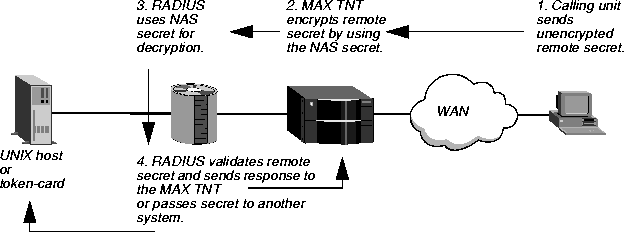
Figure 3-6. How PAP works
How CHAP and MS-CHAP work
For CHAP and MS-CHAP authentication, the following events take place:
- The MAX TNT sends a random, 128-bit challenge to the calling unit.
- The calling unit calculates an MD5 digest by means of the remote secret, the challenge,
and the PPP packet ID.
- The calling unit sends the MD5 digest, the challenge, and the PPP packet ID (but not the
remote secret) to the MAX TNT.
The MAX TNT never has the remote secret.
- The MAX TNT forwards the digest, along with the original challenge and PPP packet ID,
to RADIUS.
No encryption is necessary, because MD5 creates a one-way code that cannot be decoded.
- The RADIUS server looks up the remote secret in a local database, and calculates an MD5
digest with the local version of the remote secret, along with the challenge and PPP packet
ID received from the MAX TNT.
- The RADIUS server compares the calculated MD5 digest with the digest it received from
the MAX TNT.
If the digests are the same, the remote secrets used by the calling unit and the RADIUS server are the same, and the MAX TNT authenticates the call.
Figure 3-7 illustrates how CHAP and MS-CHAP work.
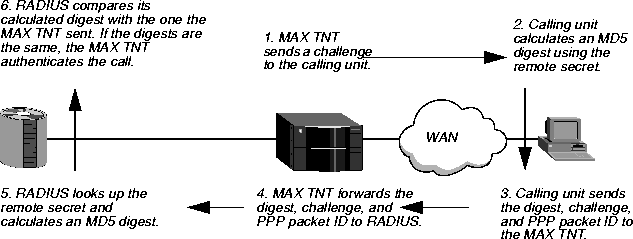
Figure 3-7. How CHAP and MS-CHAP work
Requesting an access protocol for outgoing calls
If you want to request an authentication protocol for an outgoing PPP or MP+ call, you must use the attributes described in Table 3-6. These attributes represent the minimum you must set to request an authentication protocol.
To request an access protocol for outgoing calls:
- On the first line of the profile, set the User-Name attribute to the name of the device that
will receive outgoing calls, and append -Out to the user name.
- Set the Password attribute to "ascend".
- Set User-Service=Dialout-Framed-User.
- On the second line, set the User-Name attribute to the name of the device that will receive
outgoing calls.
- On any succeeding line, set Framed-Protocol=PPP (for a PPP call), or MPP (for an MP+
call).
- Set the Ascend-Send-Auth attribute to specify an authentication protocol for an outgoing
PPP or MP+ call.
The MAX TNT requests the authentication protocol you specify when it initiates a connection with PPP or MP+ encapsulation. The answering side of the connection determines which authentication protocol, if any, the connection uses.
- If you request PAP or CHAP authentication, you must specify a password with
Ascend-Send-Secret or Ascend-Send-Passwd.
Example of requesting CHAP for an outgoing call
In Figure 3-8, the MAX TNT makes an outgoing PPP call to a client on the 10.5.0.0/24 subnet.
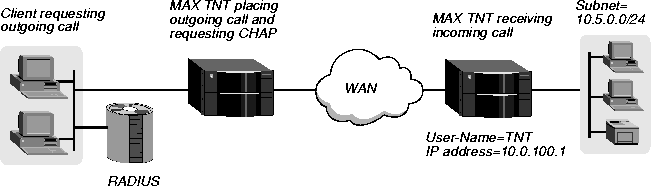
Figure 3-8. Requesting CHAP authentication
For requesting CHAP, the profile must include values for the Ascend-Send-Auth and Ascend-Send-Secret attributes. In this example, you might configure the profile as follows:
TNT-Out Password="ascend", User-Service=Dialout-Framed-User
User-Name="TNT",
Ascend-Send-Auth=Send-Auth-CHAP,
Ascend-Send-Secret="passwrd1",
Ascend-Dial-Number="31",
Framed-Protocol=PPP,
Framed-Address=10.0.100.1,
Framed-Netmask=255.255.255.0,
Ascend-Metric=2,
Framed-Routing=None,
Framed-Route="10.5.0.0/24 10.0.100.1 1",
Ascend-Idle-Limit=30
Setting up the MAX TNT for callback
You have the option of setting up callback security on the MAX TNT. This type of security instructs the MAX TNT to hang up and call back when it receives an incoming call. You can require callback to ensure that the MAX TNT makes a connection with a known device. You can specify callback for switched lines only.
To set up the MAX TNT for callback, use the attributes listed in Table 3-7.
To configure the MAX TNT for callback:
- Set Ascend-Callback=Callback-Yes.
- Set Ascend-Dial-Number to the phone number of the remote device. (The MAX TNT can
also use the CLID in order to reach the remote end of the connection, if the CLID is
available.)
- Set Ascend-Send-Secret or Ascend-Send-Passwd. (Use Ascend-Send-Passwd only if your
version of the MAX TNT does not support Ascend-Send-Secret.)
When you set Ascend-Callback=Callback-Yes, the following events occur:
- The MAX TNT hangs up after receiving an incoming call that matches the one specified
in the RADIUS user profile.
- The MAX TNT uses the following values to call back the device at the remote end of the
link:
- Number specified by the Ascend-Dial-Number attribute or the CLID.
- Password specified by Ascend-Send-Secret or Ascend-Send-Passwd.
If you set up a RADIUS user profile for callback and CLID-only authentication, the MAX TNT never answers the call. The caller therefore avoids billing charges.
Example of configuring the MAX TNT for callback
In Figure 3-9, the user named Emma dials in, and the MAX TNT hangs up and calls back.
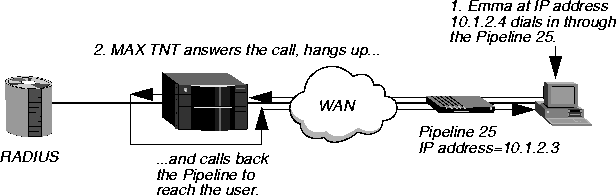
Figure 3-9. Setting up callback
When the MAX TNT calls back, it requests PAP authentication over an MP+ link. In this example, you would configure Emma's user profile as follows:
Emma Password="pwd"
User-Service=Framed-User,
Ascend-Data-Svc=Switched-56K,
Ascend-Maximum-Time=180,
Ascend-Dial-Number=555-1213,
Framed-Route="10.1.2.4 10.1.2.3",
Ascend-Callback=Callback-Yes,
Framed-Protocol=MPP,
Framed-Address=10.1.2.3,
Ascend-Send-Auth=Send-Auth-PAP,
Ascend-Send-Passwd="test"
Setting up CLID authentication
If you choose, you can require RADIUS to authenticate incoming calls by checking the calling party's phone number. The RADIUS server performs Calling-Line ID (CLID) authentication before enabling the MAX TNT to answer an incoming call. The CLID is the phone number of the calling device, which is not always provided by the WAN carrier. When the profile requires CLID authentication, the telco-provided caller ID must match a phone number specified in a local Connection profile or RADIUS user profile. You can thereby ensure that the call comes from a known source.
This section describes how to set up a RADIUS user profile for CLID authentication. Before you begin your RADIUS configuration, you must set the CLID-Auth-Mode parameter at the MAX TNT configuration interface. If you choose, you can also set other optional parameters.
Then, when you configure RADIUS, you can choose from the following configurations:
- Authenticate all callers using name, password, and caller ID. (For details, see CLID authentication using a name, password, and caller ID.-)
- Authenticate all callers using a caller ID only. (For details, see CLID authentication using a caller ID only.)
- Use an external authentication server, such as a token-card authentication server, to authenticate users after CLID authentication. (For details, see External authentication after CLID authentication.)
- Request PAP, CHAP, or MS-CHAP after CLID authentication. (For details, see PAP, CHAP, or MS-CHAP after CLID authentication.)
Configuring CLID authentication at the MAX TNT interface
Before you set up CLID authentication in RADIUS, you must set the CLID-Auth-Mode parameter in the Answer-Defaults profile. The settings are described in Table 3-8.
Table 3-8. CLID-Auth-Mode settings for CLID authentication
Setting
|
Description
|
|---|
|
CLID-Prefer
|
If you want to authenticate callers by name, password, and caller ID, choose CLID-Prefer.
CLID-Prefer specifies that whenever the CLID is available, the MAX TNT checks the calling party's phone number against the value of the Caller-Id attribute in a RADIUS user profile. If it finds a match, and the profile does not require any further authentication, the MAX TNT accepts the call. If the CLID is not available, or if the MAX TNT cannot find a match to the calling-party number, the MAX TNT uses the authentication method specified by the Answer-Defaults profile.
|
CLID-Require
CLID-Fallback
|
If you want to authenticate callers by caller ID only, choose CLID-Require or CLID-Fallback.
CLID-Require specifies that the calling party's phone number must match the value of the Caller-Id attribute before the MAX TNT can answer the call. If CLID is not available, the MAX TNT does not answer the call.
CLID-Fallback handles the case of RADIUS server timeouts. If the RADIUS server query times out so that CLID authentication cannot be completed, the MAX TNT does not drop the call. Instead it looks for a resident Connection profile to use for standard PAP, CHAP, MS-CHAP, or terminal-server authentication. Therefore, if you set CLID-Auth-Mode to CLID-Fallback, you must also set up a Connection profile.
|
General guidelines for CLID authentication
Before you set up CLID authentication, consider the following:
- In some installations, the WAN provider might not be able to deliver CLIDs, or a caller might choose to keep a CLID private.
- CLID authentication applies only if CLID is available end-to-end and Automatic Number Identification (ANI) applies to the call.
- T1 access lines and Switched-56 lines do not support CLID.
- When a user dials into the MAX TNT with MP or MP+, the calling device might have more than one phone number associated with it. In that case, the CLID is the phone number associated with the channel in use.
CLID authentication using a name, password, and caller ID
To set up CLID authentication using name, password, and caller ID, use the attributes listed in Table 3-9.
To require all callers to use name, password, and caller ID for authentication, first set CLID-Auth-Mode=CLID-Prefer in the Answer-Defaults profile on the MAX TNT. Then, for the first line of all dial-in RADIUS user profiles, use the following format:
username Password="password", Caller-Id="phonenum"
- username is the user name.
- password is the user's password.
- phonenum is the caller ID.
Although you can configure local Connection profiles for authentication using name, password, and caller ID, Ascend recommends that you perform this function in RADIUS.
Example of CLID authentication using a name, password, and caller ID
Figure 3-10 shows how to set up CLID authentication for Emma by means of a name, password, and caller ID. Emma reaches the MAX TNT through a PPP dial-in connection across the WAN.
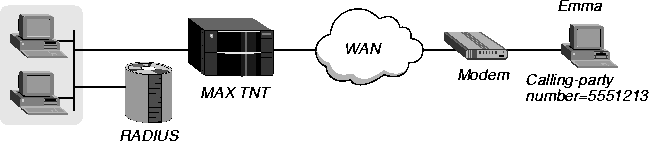
Figure 3-10. Setting up CLID authentication using a name, password, and caller ID
The user profile specifies the name, password, and caller ID on the first line. In this example, you would configure Emma's user profile as follows:
Emma Password="test", Caller-Id="5551213"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=255.255.255.254,
Framed-Netmask=255.255.255.255,
Ascend-Assign-IP-Pool=1,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Idle-Limit=30
CLID authentication using a caller ID only
To set up CLID authentication using a caller ID only, use the attributes listed in Table 3-10.
Although you can configure local Connection profiles for authentication that uses a caller ID only, Ascend recommends that you perform this function in RADIUS. To require all callers to use a caller ID only for authentication, proceed as follows:
- If you have not done so already, set CLID-Auth-Mode=CLID-Require or CLID-Fallback
in the Answer-Defaults profile on the MAX TNT.
- In all dial-in RADIUS user profiles, set up the first line in the following format:
phonenum Password="Ascend-CLID" Caller-Id="phonenum"
where the phonenum argument is the calling party's phone number. The Password value specifies that RADIUS authenticates the caller by caller ID only.
- On a subsequent line of all dial-in profiles, set the Ascend-Require-Auth attribute to
Not-Require-Auth.
Example of CLID authentication using a caller ID only
Figure 3-11 shows how to set up CLID authentication that uses a caller ID only. The user at IP address 255.255.255.254 reaches the MAX TNT through a PPP dial-in connection across the WAN.
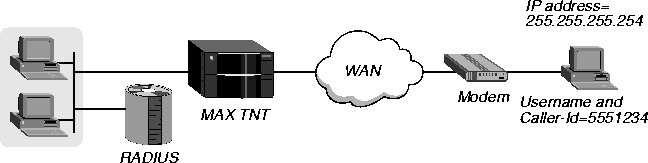
Figure 3-11. Setting up CLID authentication using a caller ID only
The user profile specifies the calling-party number as both the username and the caller ID. In this example, you would configure the user profile as follows:
5551234 Password="Ascend-CLID", Caller-Id="5551234"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=255.255.255.254,
Framed-Netmask=255.255.255.255,
Ascend-Assign-IP-Pool=1,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Idle-Limit=30
External authentication after CLID authentication
You can use an external authentication server, such as a token-card server, to authenticate callers after CLID authentication. All users must pass caller-ID authentication and external authentication. The configuration uses a two-tiered setup, with the attributes listed in Table 3-11.
To set up external authentication after CLID authentication, proceed as follows:
- If you have not done so already, set CLID-Auth-Mode=CLID-Require in the
Answer-Defaults profile on the MAX TNT.
- For the first profile of a two-tiered dial-in setup, specify only these two lines:
phonenum Password="Ascend-CLID", Caller-Id="phonenum"
Ascend-Require-Auth=Require-Auth
where the phonenum argument is the calling party's phone number.
- Configure the second-tier user profile with the following format for the first line:
Default Password="SAFEWORD" or Default Password="ACE"
- On the second and succeeding lines of the second-tier profile, specify the characteristics of
the call.
Example of using a token-card server after CLID authentication
In Figure 3-12, a user with a token card calls into the MAX TNT from the phone number 555-1212. After CLID authentication that uses a caller ID only, the user is authenticated by an Enigma Logic SafeWord server.
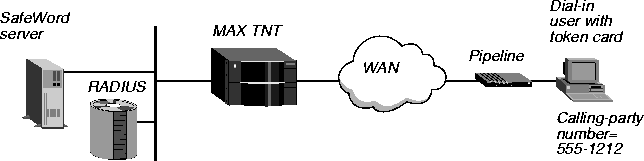
Figure 3-12. Using a token-card server after CLID authentication
In the configuration for this example, you would use two user profiles. You would configure the first profile, as follows, to perform CLID authentication and specify that additional authentication follows:
5551212 Password="Ascend-CLID", Caller-Id="5551212"
Ascend-Require-Auth=Require-Auth
You would configure the second profile to set up authentication through the SafeWord server:
Default Password="SAFEWORD"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.0.5.1,
Framed-Netmask=255.255.255.0,
Ascend-Receive-Secret="b5XSAM"
If the caller passes both authentications, the MAX TNT grants access. The Default user profile specifies the characteristics of the call.
PAP, CHAP, or MS-CHAP after CLID authentication
Following CLID authentication, you can indicate whether the MAX TNT should request Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), or MS-CHAP authentication for incoming calls on a PPP or MP+ connection.
You specify PAP, CHAP, or MS-CHAP authentication using a two-tiered method with the attributes listed in Table 3-12.
To request PAP, CHAP, or MS-CHAP authentication after CLID authentication, you must set the Receive-Auth-Mode parameter in the PPP-Answer subprofile of the Answer-Defaults profile. Then, you must configure two RADIUS user profiles, as described in the following sections.
Configuring the first-tier profile
In RADIUS, set up a first-tier profile specifying CLID authentication, setting only the attributes described in the following steps:
- Set the User-Name attribute to the calling party's phone number.
- Set the Password attribute to "Ascend-CLID".
- Set the Caller-Id attribute to the calling party's phone number.
- Set the Ascend-Require-Auth attribute to Require-Auth.
Calls that have been CLID authenticated undergo no further authentication unless the matching RADIUS entry has Ascend-Require-Auth=Require Auth. If Ascend-Require-Auth=Require Auth, the parameters of the call are initially set by CLID authentication, but are subject to change by any authentication that might follow.
Configuring the second-tier profile
You specify the characteristics of the call in the second-tier user profile. Proceed as follows:
- In the first line, specify the User-Name and Password attributes.
- On the same line as the User-Name and Password attribute, set the Caller-Id attribute to
the phone number you specified for User-Name in the first-tier user profile.
- On any succeeding lines, set the User-Service=Framed-User and Framed-Protocol=PPP.
- Specify any additional attributes.
Example of using CHAP after CLID authentication
In this example, the MAX TNT first authenticates the user by means of a caller ID only, and then requires CHAP. The user named Virginia dials in over a PPP connection with IP routing. In the PPP-Answer subprofile of the Answer-Defaults profile, the Receive-Auth-Mode parameter is set to CHAP-PPP-Auth. Figure 3-13 illustrates the WAN configuration.
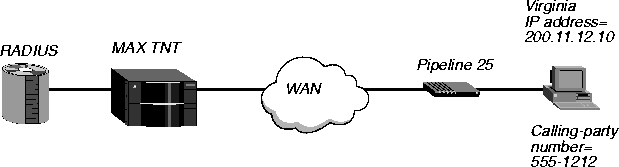
Figure 3-13. Using CHAP after CLID authentication
The following profiles show a two-tiered approach. First, the administrator configures a user profile specifying CLID authentication, and indicating that additional CHAP authentication will follow:
5551212 Password="Ascend-CLID", Caller-Id="5551212"
Ascend-Require-Auth=Require-Auth
Then, the administrator configures a second user profile setting up other attributes for the call:
Virginia Password="pwd", Caller-Id="5551212"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.11.12.10,
Framed-Netmask=255.255.255.248
Ascend-Assign-IP-Pool=1,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Idle-Limit=30
Setting up called-number authentication
If you choose, you can set up called-number authentication. This type of authentication works much like CLID authentication, except that the MAX TNT uses the called-party number to authenticate the connection. The remote end might use this form of authentication to make sure that the call goes to a known destination.
The called-party number is an information element of the Q.931 ISDN signaling protocol. It is the phone number the remote device calls to connect to the MAX TNT, but without a trunk group or dialing prefix specification. This number is always available if specified in a profile. When the profile requires called-number authentication, the number called must match a phone number in a local Connection profile or RADIUS user profile.
This section describes how to set up a RADIUS user profile for called-number authentication. Before you begin your RADIUS configuration, you must set the CLID-Auth-Mode parameter at the MAX TNT configuration interface. Then, when you configure RADIUS, you can choose from the following configurations:
Configuring called-number authentication at the MAX TNT interface
Before you set up CLID authentication in RADIUS, you must set the CLID-Auth-Mode parameter in the Answer-Defaults profile. Use either of the settings described in Table 3-13.
Table 3-13. CLID-Auth-Mode settings for called-number authentication
Setting
|
Description
|
|---|
|
DNIS-Prefer
|
If you want to authenticate callers by name, password, and called-party number, choose DNIS-Prefer.
DNIS-Prefer specifies that whenever the called-party number is available, the MAX TNT checks the called-party number against the value of the Client-Port-DNIS attribute in a RADIUS user profile. If it finds a match, and the profile does not require any further authentication, the MAX TNT accepts the call.
If the called-party number is not available, or if the MAX TNT cannot find a match to the called-party number, the MAX TNT applies authentication by means of the Receive-Auth-Mode parameter in the PPP-Answer subprofile of the Answer-Defaults profile.
|
|
DNIS-Require
|
If you want to authenticate callers by called-party number only, choose DNIS-Require. This setting indicates that the called-party number must match the value of the Client-Port-DNIS attribute before the MAX TNT can answer the call. If the called-party number is not available, the MAX TNT does not answer the call.
|
Authentication using a name, password, and called-party number
To set up name, password, and called-number authentication, use the attributes listed in Table 3-14.
To require all callers to use name, password and called-party number for authentication, first set CLID-Auth-Mode=DNIS-Pref in the Answer-Defaults profile on the MAX TNT. Then, for the first line of all dial-in RADIUS user profiles, use the following format:
username Password="password", Client-Port-DNIS="phonenum"
- username is the user name.
- password is the user's password.
- phonenum is the called-party number.
Although you can configure local Connection profiles for authentication that uses name, password, and called-party number, Ascend recommends that you perform this function in RADIUS.
Example using a name, password, and called-party number
Figure 3-14 shows how to set up called-number authentication for Emma by means of a name, password, and called-party number. Emma reaches the MAX TNT through a PPP dial-in connection across the WAN.
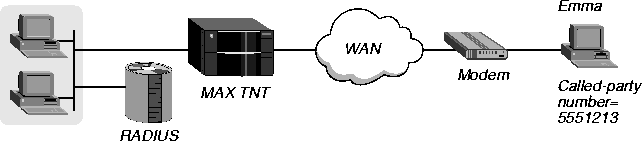
Figure 3-14. Setting up authentication using a name, password, and called-party number
Emma is at IP address 255.255.255.254. You would configure her user profile to set up a name, password, and called-party number on the first line:
Emma Password="test", Client-Port-DNIS="5551213"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=255.255.255.254,
Framed-Netmask=255.255.255.255,
Ascend-Assign-IP-Pool=1,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Idle-Limit=30
Authentication using the called-party number only
To set up authentication by called-party number only, use the attributes listed in Table 3-15.
Although you can configure local Connection profiles for authentication that uses the called-party number only, Ascend recommends that you perform this function in RADIUS. To require all callers to use only the called-party number for authentication, proceed as follows:
- If you have not done so already, set CLID-Auth-Mode=DNIS-Require in the
Answer-Defaults profile on the MAX TNT.
- In all dial-in RADIUS user profiles, set up the first line in the following format:
phonenum Password="Ascend-DNIS", Client-Port-DNIS="phonenum"
where the phonenum argument is the called-party number. The Password value specifies that RADIUS authenticates the caller by called-party number only.
- On a subsequent line of all dial-in profiles, set the Ascend-Require-Auth attribute to
Not-Require-Auth.
Example of authentication using the called-party number only
Figure 3-15 shows how to set up called-number authentication by means of the called-party number only.
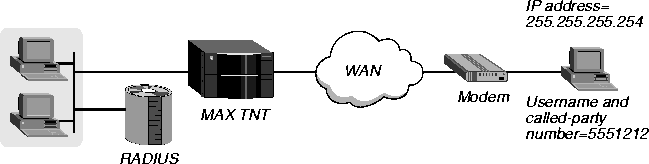
Figure 3-15. Setting up called-number authentication using the called-party number only
The user at IP address 255.255.255.254 reaches the MAX TNT through a PPP dial-in connection across the WAN. The first line of the user profile specifies the called-party number as both the username and the value of Client-Port-DNIS. In this example, you would configure the user profile as follows:
5551212 Password="Ascend-DNIS", Client-Port-DNIS="5551212"
Ascend-Require-Auth=Not-Require-Auth,
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=255.255.255.254,
Framed-Netmask=255.255.255.255,
Ascend-Assign-IP-Pool=1,
Ascend-Route-IP=Route-IP-Yes,
Ascend-Idle-Limit=30
External authentication after called-number authentication
You can use an external authentication server, such as a token-card server, to authenticate callers after called-number authentication. All users must pass called-number authentication and external authentication. The configuration uses a two-tiered setup, with the attributes listed in Table 3-16.
To set up external authentication after called-number authentication, proceed as follows:
- If you have not done so already, set CLID-Auth-Mode=DNIS-Require in the
Answer-Defaults profile on the MAX TNT.
- For the first profile of a two-tiered dial-in setup, specify only these two lines:
phonenum Password="Ascend-DNIS", Client-Port-DNIS="phonenum"
Ascend-Require-Auth=Require-Auth
where the phonenum argument is the called-party number.
- Configure the second-tier user profile with the following format for the first line:
Default Password="SAFEWORD" or Default Password="ACE"
- On the second and succeeding lines of the second-tier profile, specify the characteristics of
the call.
Example of using token-card after called-number authentication
In Figure 3-16, a user with a token card calls into the MAX TNT from the phone number 555-1212. After passing called-number authentication that uses the calling-party number only, the user is authenticated by an Enigma Logic SafeWord server.
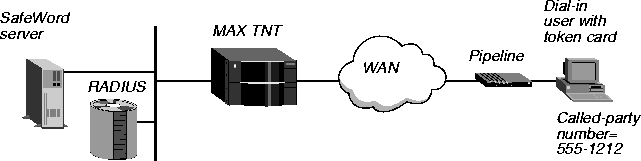
Figure 3-16. Using a token-card server after called-number authentication
In the configuration for this example, you would use two use profiles. You would configure the first profile, as follows, to set up called-number authentication and to specify that additional authentication follows:
5551212 Password="Ascend-DNIS", Client-Port-DNIS="5551212"
Ascend-Require-Auth=Require-Auth
You would configure the second profile to set up authentication through the SafeWord server:
Default Password="SAFEWORD"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.0.5.1,
Framed-Netmask=255.255.255.0,
Ascend-Receive-Secret="b5XSAM"
The first pass checks the called-party number. The second pass checks the name and password through the token-card server. If the caller passes both authentications, the MAX TNT grants access. The Default user profile specifies the characteristics of the call.
Setting up token-card authentication
This section begins with a discussion of how token-card authentication works. It then discusses each step for configuring token-card authentication at your site.
You must choose PAP-Token, Cache-Token, or PAP-Token-CHAP authentication, and make the appropriate settings. (For details, see Configuring PAP-Token authentication, Configuring Cache-Token authentication, and Configuring PAP-Token-CHAP authentication.)
You also have the option of configuring ACE authentication for users behind a remote router. (For instructions, see Configuring ACE authentication for remote router users.)
Note: You can use RADIUS to set up token-card authentication of incoming calls only. If you
want to configure the MAX TNT as the calling unit and enable local token-card users to call a
remote site, you must configure a Connection profile in the MAX TNT configuration interface.
For details, see the MAX TNT Network Configuration Guide.
Introducing token-card authentication
You can set up your network site to require that users change passwords many times per day. When you do so, you use an external authentication server, such as a Security Dynamics ACE/Server or an Enigma Logic SafeWord server. The external server syncs up with hand-held personal token cards. These devices are the size and shape of a credit card. The token card provides a user with a current password in real time. This password is called a token. The LCD on the user's card displays the current, one-time-only token required to gain access at that moment to the secure network.
Figure 3-17 illustrates an environment that includes an Ascend Pipeline as the calling unit, an NAS (the MAX TNT), a RADIUS server, and an external authentication server.
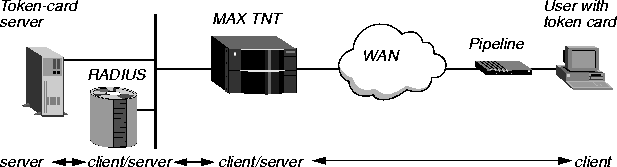
Figure 3-17. Using an external authentication server
When you use token-card authentication, the following events take place:
- A user attempts to open a connection to the MAX TNT, sending his or her user name.
This user is a client of the MAX TNT. The user can be in terminal-server mode or, alternatively, use the APP Server utility. Ascend Password Protocol (APP) is a UDP protocol from Ascend. When authentication is complete, the user can switch to PPP mode.
- The MAX TNT determines that it must use a RADIUS user profile to authenticate the
user.
- The MAX TNT sends the user's connection request to the RADIUS server in an
Access-Request packet.
The MAX TNT is a client of the RADIUS server.
- The RADIUS server forwards the connection request to the ACE or SafeWord client,
which resides on the same system as RADIUS.
- An ACE client forwards the information to the ACE/Server authentication server. A
SafeWord client forwards the information to the SafeWord authentication server.
In either case, the RADIUS server is a client of the authentication server.
- The authentication server sends an Access-Challenge packet back through the RADIUS
server and the MAX TNT to the user dialing in.
- The user sees the challenge message and obtains the current token from his or her token
card.
If the authentication server is an ACE/Server, the user has a SecurID token card that displays a randomly generated access code. The code changes every 60 seconds.
If the authentication server is a SafeWord server, the user can have one of the following types of token cards:
- ActivCard
- CryptoCard
- DES Gold
- DES Silver
- SafeWord SofToken
- SafeWord MultiSync
- DigiPass
- SecureNet Key
- WatchWord
- The user enters the current token obtained from the token card in response to the challenge
message.
- The token travels back through the NAS and the RADIUS server to the authentication
server.
- The authentication server sends a response to the RADIUS server, specifying whether the
user has entered the proper user name and password.
If the user enters an incorrect password, the ACE/Server or SafeWord server returns another challenge, and the user can again attempt to enter the correct password. The server sends up to three challenges. After three incorrect entries, the MAX TNT terminates the call.
- The RADIUS server sends an authentication response to the MAX TNT.
If authentication is unsuccessful, the MAX TNT receives an Access-Reject packet. If authentication is successful, the MAX TNT receives an Access-Accept packet. The packet contains a list of attributes from the user profile in the RADIUS server's database. The MAX TNT then establishes network access for the caller.
Configuring PAP-Token authentication
PAP-Token specifies an extension of PAP authentication. In PAP-Token, the user authenticates his or her identity by entering a password (called a token). The token is derived from a hardware device, such as a hand-held token card. The MAX TNT prompts the user for the token, possibly along with a challenge key. The MAX TNT obtains the challenge key from a token-card server that it accesses through RADIUS. The token travels in the clear, but because it is a one-time-only password, the security risk is usually not serious. To authenticate the base channel of the connection, the token-card server uses the token that the user sends in response to the challenge.
PAP-Token is appropriate for single-channel, dial-out calls. It is not practical for multichannel calls, because any time that bandwidth requirements cause another channel to come up, the MAX TNT challenges the user for another token. To set up PAP-Token authentication, use the attributes listed in Table 3-17.
To set up PAP-Token authentication, set the User-Name attribute to the remote router's system name. Then, specify "SAFEWORD" or "ACE" for the Password attribute. By setting the Password attribute to "SAFEWORD", you can request validation from an Enigma Logic SafeWord server. For example:
Mike Password="SAFEWORD"
By setting the Password attribute to "ACE", you can request validation from a Security Dynamics ACE server. For example:
Connor Password="ACE"
Example of using PAP-Token with a Security Dynamics ACE/Server
This example shows how to set up RADIUS for use with the Security Dynamics ACE/Server. The remote end consists of a Pipeline 50 unit and a PC running Appserv. The local end consists of a MAX TNT and a UNIX device running RADIUS, ACE/Client, and ACE/Server. Figure 3-18 illustrates the WAN configuration.
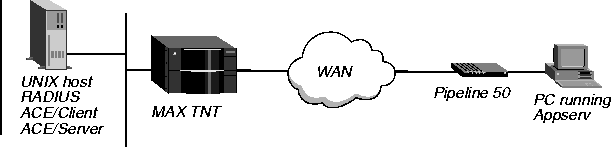
Figure 3-18. Setting up PAP-Token with an ACE/Server
At the remote end, the Appserv process constantly monitors for authentication requests. When it receives one from the Pipeline 50, it sends the request to the MAX TNT. The MAX TNT tries to match the caller's name to the value of the Station parameter in a Connection profile. If the MAX TNT does not find a match, and you have enabled RADIUS, the MAX TNT forwards the request to RADIUS. RADIUS then checks its profiles. If it finds one whose password is set to ACE, it requests that Appserv prompt the Pipeline 50 for a passcode. The authentication server then checks the passcode against the name assigned the Pipeline 50.
To modify an existing profile for ACE/Server authentication, simply change the password to "ACE", as in the following example:
Connor Password="ACE"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.72.138.1,
Framed-Netmask=255.255.255.0,
Ascend-Idle-Limit=300,
Framed-Routing=None
Configuring Cache-Token authentication
Cache-Token authentication uses a shared secret, and simplifies the authentication process by caching the user's token for the fixed length of time specified by the Ascend-Token-Expiry attribute. During the lifetime of the token, subsequent calls by the user require only CHAP authentication without the use of a hand-held token card. When the cached token expires, the ACE or SAFEWORD server authenticates Cache-Token access requests.
To set up Cache-Token authentication, use the attributes listed in Table 3-18. Except for the Ascend-Receive-Secret attribute, all attributes must appear on the first line of the user profile.
To set up Cache-Token authentication:
- Set the User-Name attribute to the remote router's system name.
- Specify "SAFEWORD" or "ACE" for the Password attribute.
If you specify "ACE", the MAX TNT can authenticate multiple users behind the remote router. For details, see Configuring ACE authentication for remote router users. This feature is not available if you specify the "SAFEWORD" setting.
- Set the Ascend-Token-Expiry attribute to the lifetime in minutes of a cached token.
- If you want to specify the maximum length of time in minutes a cached token can remain
alive between authentication, set the Ascend-Token-Idle attribute (optional).
This attribute is useful for enforcing authentication when a connection comes up again after an idle period. If you do not specify this attribute, the cached token remains alive until the value of the Ascend-Token-Expiry attribute causes it to expire. Typically, the value of Ascend-Token-Idle is lower than the value of Ascend-Token-Expiry.
- If the user profile contains the setting User-Service=Login-User, and the token-card server
requires that a user enter a challenge, set Ascend-Token-Immediate=Tok-Imm-No.
When you set Ascend-Token-Immediate=Tok-Imm-No, RADIUS ignores the user's password. If you specify, Tok-Imm-Yes, RADIUS sends the password to the security server for authentication.
- Set the Ascend-Receive-Secret attribute to the same password as the Send-Password
parameter in the Connection profile at the remote end.
The RADIUS server uses this value to authenticate incoming calls from a user while his or her token is cached and alive. The cached token resides on the MAX TNT during the initial token-card authentication process.
- When you start the RADIUS daemon, specify the
-c argument to enable cache-token
authentication.
Example of using Cache-Token with an Enigma Logic SafeWord server
Figure 3-19 shows a setup in which a user called John uses an Enigma Logic SafeWord server. After MP+ authentication, the user receives the IP address 200.0.5.1 and subnet mask 255.255.255.0. RADIUS sends the password to the security server for authentication.
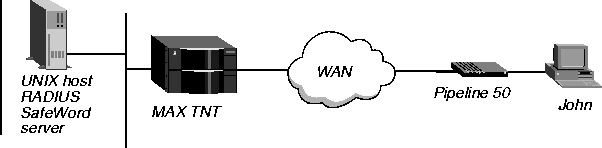
Figure 3-19. Setting up Cache-Token with a SafeWord server
In this example, you would configure John's user profile as follows:
John Password="SAFEWORD", Ascend-Token-Expiry=90,
Ascend-Token-Idle=80, Ascend-Token-Immediate=Tok-Imm-Yes
Ascend-Receive-Secret="shared-secret",
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.0.5.1,
Framed-Netmask=255.255.255.0
(The printed page forces a break in the first line. However, you must enter the Ascend-Token-Expiry, Ascend-Token-Idle, and Ascend-Token-Immediate attributes on the first line of the profile.)
Configuring PAP-Token-CHAP authentication
PAP-Token-CHAP authentication uses PAP-Token to authenticate the base channel of an MP+ call, and then a CHAP password to authenticate additional channels. The advantage of a PAP-Token-CHAP call over a PAP-Token call is that you need to verify only the initial connection by means of a hand-held token card. In a PAP-Token-CHAP call, the MAX TNT uses CHAP to verify any additional channels.
To set up PAP-Token-CHAP authentication, use the attributes listed in Table 3-19.
To set up PAP-Token-CHAP authentication:
- Set the User-Name attribute to the remote router's system name.
- Specify "SAFEWORD" or "ACE" for the Password attribute.
- Set Ascend-Receive-Secret to the value of the Aux-Send-Password parameter specified in
the remote end's Connection profile.
The RADIUS server sends this value to your MAX TNT in order to verify an encrypted password.
Whenever the MAX TNT adds channels to a PPP or MP+ call with PAP-Token-CHAP, the calling unit sends the encrypted value of Aux-Send-Password, and the answering unit checks this password against Ascend-Receive-Secret. The answering unit receives Ascend-Receive-Secret from the RADIUS server when the first channel of the call connects.
Example of using PAP-Token-CHAP with a SafeWord server
Figure 3-20 shows a setup in which a user called Emma uses an Enigma Logic SafeWord server. After authentication, the user can open an MP+ (or PPP) session. The user receives IP address 200.0.5.1 and subnet mask 255.255.255.0.
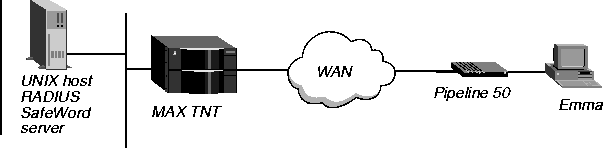
Figure 3-20. Setting up PAP-Token-CHAP with a SafeWord server
Because Emma's user profile includes the Ascend-Receive-Secret attribute, the MAX TNT can authenticate additional channels through CHAP without having to go to the SAFEWORD server for authentication each time. In this example, you would configure Emma's user profile as follows:
Emma Password="SAFEWORD"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.0.5.1,
Framed-Netmask=255.255.255.0,
Ascend-Receive-Secret="b5XSAM"
Configuring ACE authentication for remote router users
You can specify that the RADIUS server use an ACE entry to authenticate multiple users behind a single remote router (such as an Ascend Pipeline unit). To set up this type of configuration, use the attributes listed in Table 3-20.
First, set the User-Name attribute to the remote router's system name. Then, specify "ACE" for the Password attribute. The user must enter the token in this format:
password.realname
The realname argument is the user's real name. The RADIUS server presents the realname argument, rather than the name of the Pipeline, to the ACE server. Token caching still functions normally. All users share the same profile, and all accounting uses the Pipeline name, not the real user name.
Example of setting up ACE authentication for remote router users
In Figure 3-21, multiple remote users are connected to a Pipeline 50 called Alameda.
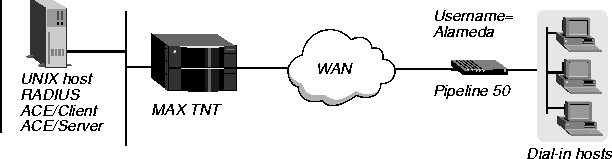
Figure 3-21. Setting up ACE authentication for remote router users
The user profile specifies the system name of the Pipeline 50 and the password for ACE authentication. In this example, you would configure the profile as follows:
Alameda Password="ACE"
User-Service=Framed-User,
Framed-Protocol=PPP,
Framed-Address=200.72.138.1,
Framed-Netmask=255.255.255.0,
Ascend-Idle-Limit=300,
Ascend-Route-IP=Route-IP-Yes
Setting up authentication for terminal-server calls
This section describes how to set up authentication for the following configurations:
- Terminal-server calls with PAP, CHAP, or MS-CHAP
- Asynchronous PPP calls using terminal-server authentication
- Digital dial-in using terminal-server authentication
Configuring terminal-server calls with PAP, CHAP, or MS-CHAP
Table 3-21 lists the types of equipment that allow a customer to communicate with PPP and PAP, CHAP, or MS-CHAP authentication.
In Figure 3-22, the dial-in client is connected to an ISDN TA performing asynchronous to synchronous conversion. The connection between the client and the TA is asynchronous, and the ISDN connection between the TA and the MAX TNT is synchronous.
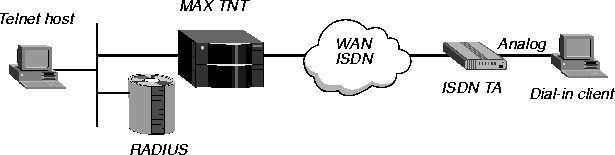
Figure 3-22. A terminal-server connection by means of an ISDN TA with asynchronous PPP
The following events take place:
- The client calls and the MAX TNT answers.
- The MAX TNT waits for PPP packets, as specified by the RADIUS user profile or a local
Connection profile.
- The client sends PPP packets.
- The MAX TNT responds with PPP, and LCP negotiation starts.
- The MAX TNT carries out PAP, CHAP, or MS-CHAP authentication.
- After authentication, upper layer NCPs (IPCP, IPXCP, CCP) are negotiated.
- The client device and the MAX TNT communicate using PPP over the ISDN line.
For information about setting up PAP, CHAP, or MS-CHAP authentication, see Specifying an access protocol for incoming calls.
Configuring asynchronous PPP and terminal-server authentication
Figure 3-23 illustrates a dial-in user initiating a terminal-server session through an asynchronous PPP connection.
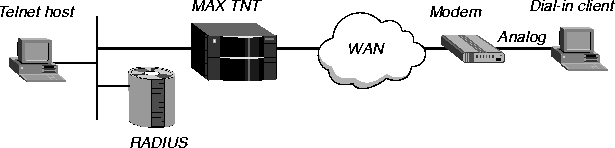
Figure 3-23. A terminal-server connection using asynchronous PPP
If a customer is using asynchronous PPP, dialing in over an analog line, and will undergo terminal-server authentication, proceed as follows:
- If the user will make use of the terminal-server interface and then use PPP, set
User-Service=Login-User.
- If the user will bypass the terminal-server interface and use PPP, set
User-Service=Framed-User.
- If User-Service=Login-User, set PPP=Yes in the PPP-Mode-Configuration subprofile of
the Terminal-Server profile.
- If User-Service=Login-User, your customer's PPP software must have an expect-send
script, at the end of which the user starts sending PPP packets.
For analog dial-in using asynchronous PPP and terminal-server authentication, the following events take place:
- The client calls with an analog modem, and the MAX TNT answers.
- The MAX TNT waits for PPP packets, while the client software expects the
terminal-server login prompt.
- The MAX TNT times out on PPP, and sends the login prompt.
- The client software sees the login prompt, enters a user name, and waits, expecting the
password prompt.
- The MAX TNT sends the password prompt, and the client sends a password.
- The MAX TNT authenticates the user name and password against a RADIUS profile or
local Connection profile.
- If User-Service=Framed-User in the RADIUS user profile, the MAX TNT does not
present the
ascend% prompt, but sends PPP packets.
- If User-Service=Login-User in the RADIUS user profile, the MAX TNT presents the
ascend% prompt, and then sends PPP packets.
- The client software and the MAX TNT communicate using PPP over the asynchronous
serial analog line.
Configuring digital dial-in with terminal-server authentication
In Figure 3-24, the dial-in client is connected to an ISDN TA by a digital line.
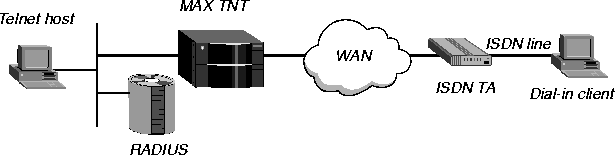
Figure 3-24. A terminal-server connection by means of an ISDN TA over a digital line
If a customer is using an ISDN TA, dialing in over a digital line, and will undergo terminal-server authentication, proceed as follows:
- If the user will make use of the terminal-server interface and then use PPP, set
User-Service=Login-User.
- If the user will bypass the terminal-server interface and use PPP, set
User-Service=Framed-User.
- If User-Service=Login-User, set PPP=Yes in the PPP-Mode-Configuration subprofile of
the Terminal-Server profile.
- In the Answer-Defaults profile, set V.120=Yes.
- Make sure that your customer's TA is configured for V.120 encapsulation.You can set
most TAs in automatic mode so the TA looks for a PPP packet from the host. If the TA
finds a PPP packet, it starts PPP negotiations. If it does not find one, it tries V.120
authentication. Once the call connects, the TA uses async/PPP for the duration of the call.
For digital dial-in, the following events take place:
- The client calls using an ISDN TA, and the MAX TNT answers the call.
- The MAX TNT waits for PPP packets, while the client software expects the terminal-
server login prompt.
- The MAX TNT times out on PPP, and sends the login prompt.
- The client software sees the login prompt, enters a user name, and waits, expecting the
password prompt.
- The MAX TNT sends the password prompt, and the client sends a password.
- The MAX TNT authenticates the user name and password against a RADIUS profile or
local Connection profile.
- If User-Service=Framed-User in the RADIUS user profile, the MAX TNT does not
present the
ascend% prompt, but sends PPP packets.
- If User-Service=Login-User in the RADIUS user profile, the MAX TNT presents the
ascend% prompt, and then sends PPP packets.
- The client software and the MAX TNT communicate using PPP over an asynchronous
line- asynchronous from the workstation to the TA, and asynchronous over V.120 from
the TA to the MAX TNT.
In this configuration, you cannot use two channels, because the MAX TNT tries to authenticate the second channel with the user name the operator presents at the terminal-server login prompt. The client software does not run an expect-send script over V.120 and the second channel, so the second channel cannot connect. Without this connection, MP or MP+ fails.
Most ISDN TAs support either V.120 clear text or asynchronous-to-PPP conversion, but not both. Therefore, if you log into a PPP server in terminal and/or scripted (ASCII text) mode, the TA goes into V.120 mode and should not dial the second B channel. If for some reason the TA does dial the second channel, it will fail to bind the two channels together and will probably drop the first channel.
In order to get the second channel to connect, you must use the authentication area and fill out the Auth.ID: field and the Password: field, and choose the appropriate authentication method, usually PAP or CHAP. If you want a second channel, you cannot use a script or the terminal.
![[Top]](../images/home.jpg)
![[Contents]](../images/contents.jpg)
![[Prev]](../images/previous.jpg)
![[Next]](../images/next.jpg)
![[Last]](../images/index.jpg)


techpubs@eng.ascend.com
Copyright © 1998, Ascend Communications, Inc. All rights
reserved.

